Decoding NIS2: Everything you need to know and how to get ready
Let’s talk NIS2. And yeah, we know that in Germany – and in many other countries – it’s still not clear when NIS2 will be enacted. But one thing is for sure: Sooner or later it will come. Ready for more food for thought? Those who take the time now to improve their IT security in preparation for NIS2 are not really doing it for NIS2. They are doing it for their own sake. Because there’s no way a hardened IT environment is bad for your business in today’s threat landscape. So much for that, let’s get back to the basics.
What is the NIS2 Directive and who is it for?
The NIS2 Directive (Directive (EU) 2022/2555) is a European Union law designed to improve cybersecurity. So far, so good. And we bet it’s no news to you. Its goal is to establish a high level of security for networks and IT systems across the EU. Building on the original NIS Directive, NIS2 broadens its scope and tightens its requirements to better address evolving cyber threats.
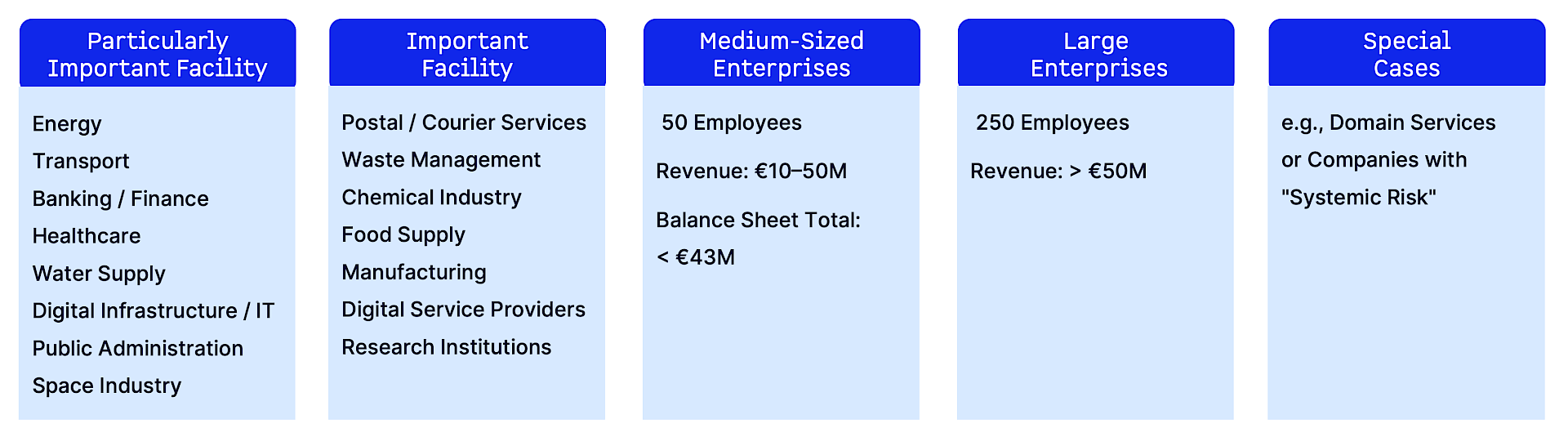
Under NIS2, affected companies (important and essential entities) must implement technical, organizational, and operational measures to manage cybersecurity risks. These measures aim to protect IT systems and networks while minimizing the impact of incidents on services or interconnected systems. Nothing wrong with improving EU cybersecurity, don’t you think? But the more important question for you is: “Am I affected?” Well, check out the graphic to find out – or just give us a call:
Goals and requirements of the Directive
Now that we know what the Directive is and who it affects, let’s dig a little deeper. What are its goals and requirements? Well, as mentioned above, the NIS2 Directive wants to sustainably improve cybersecurity in organizations. A key focus is on security risk management, including:
• Establishing clear governance structures.
• Implementing comprehensive risk management.
• Ensuring effective asset management for oversight and control of all IT systems and resources. Additionally, securing the supply chain plays a critical role in closing security gaps among partners and service providers.
To protect against cyber attacks, the Directive calls for the implementation of robust protective measures, such as:
• Clear policies and processes for securing IT services.
• Effective identity and access controls.
• Protecting sensitive data from unauthorized access or loss.
• Ensuring IT systems and networks are resilient to disruptions.
Another key area is employee awareness and training. Targeted programs should help everyone in the organization understand cybersecurity risks and respond appropriately to critical situations.
The Directive also emphasizes the importance of detecting cyber incidents. Organizations must implement continuous monitoring to oversee security events and proactively detect threats. This approach helps to mitigate attacks early and prevent potential damage.
Finally, NIS2 requires measures to minimize the impact of cyber incidents, including developing response and recovery plans to quickly restore operations after an attack. Post-incident analysis is also essential to learn lessons and reduce future risks.
Okay, let’s stop there for a minute. Because that sounds like a lot. Like, a really lot. But don’t panic. For anyone who follows basic IT security practices, NIS2 is not such a big deal. And to make your life even easier, there’s us too.
How water IT Security can support as a partner
As a specialized partner, we offer comprehensive services to help your organization comply with NIS2 requirements. And even if we think of IT security as a whole, our services can be divided into these three categories: Security Consulting, Managed SOC, ARC Disaster Recovery.
So, let’s take a look at all three and see how they can help you stay on top of your NIS2 preparations:
Security Consulting
Whether it’s basic cyber hygiene, access control concepts or the systematic use of encryption and cryptography – most of the requirements of NIS2 fall within the scope of security consulting. Here’s a quick overview of how we can support you:
1. Status Quo Analysis
• Identifying weaknesses in existing IT security strategies.
• Assessing whether and how an organization is affected by NIS2 requirements.
2. Strategic Consulting
• Developing a tailored plan to implement NIS2 requirements.
• Supporting the integration of security measures into existing business processes.
3. Technical Implementation
• Deploying solutions for risk management, monitoring, and incident response.
• Implementing advanced technologies like Intrusion Detection Systems (IDS) or Zero- Trust Architectures.
4. Training and Awareness Programs
• Educating employees to minimize human errors as a common cause of security incidents.
• Providing IT teams with the knowledge to understand current threats and security best practices.
5. Compliance Management
• Supporting adherence to reporting obligations through SOC services.
• Ensuring that all measures meet regulatory requirements.
Managed Security Operations Center (SOC)
Having the right IT security strategy in place to protect your critical assets is one thing. But monitoring your IT environment around the clock is just as important. Only when you see an attack in the first place can you respond quickly and efficiently. And let’s be honest: With 600 million identity attacks per day and a 175% increase in human-operated ransomware attacks, the question of whether your organization is a target is beside the point. It already is.
This is where our Managed Security Operations Center comes in. Our SOC experts monitor your systems 24/7 to ensure critical data is protected, allowing you to:
• Cut your need for specialized staff by 30%.
• Reduce threat detection and resolution time by up to 50%.
• Avoid up to 40% of the potential costs of a cyber attack.
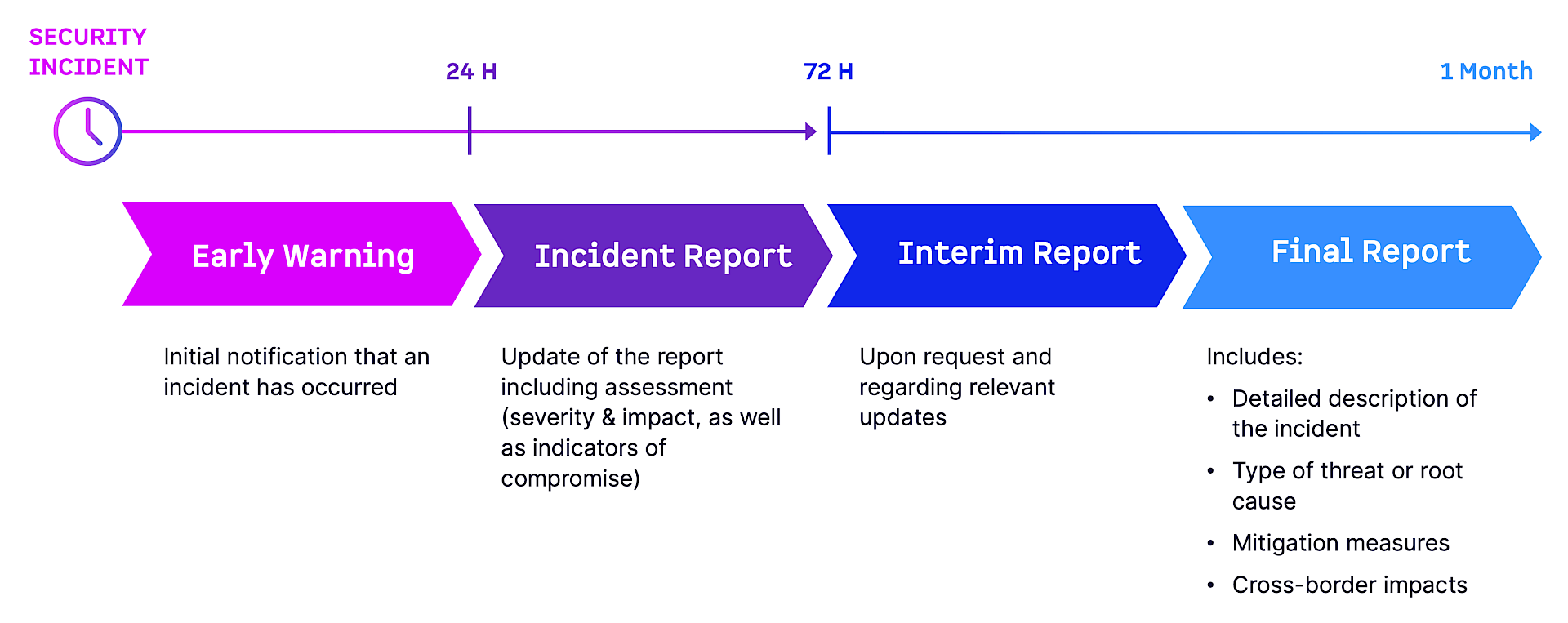
In terms of NIS2, this means: You’ll take a big step forward in security incident management – one of the key requirements of the new EU Directive.
ARC Disaster Recovery
Hopefully, the worst case will never happen. But if it does – and you have to deal with a successful cyber attack – you must remain capable of acting. Speaking from experience, many companies fail at this, which is why – you guessed it – it’s another one of the many NIS2 requirements. The answer? Resilient IT emergency management.
That’s why we developed ARC (Azure Resilient Core) – a disaster recovery solution that protects your critical processes and ensures your company remains operational in the event of an emergency. This is important for quickly coordinating countermeasures, communicating with investigating authorities if necessary, and meeting NIS2 reporting requirements. Without getting too technical, here are the three main benefits for your organization:
• Fast recovery of your critical systems.
• Minimized downtime and financial loss.
• Fits any IT environment without the need to change your existing systems.
Sanctions
Just for the sake of completeness and not to scare you: Another critical aspect of the NIS2 Directive is the potential sanctions for non-compliance.
For essential entities, fines can reach up to 10 million euros or 2% of global annual turnover, whichever is higher. For important entities, the maximum fine is capped at 7 million euros or 1.4% of global annual turnover. But if you take the time now to bring your IT security up to modern standards, you should be fine – rather than fined.
Conclusion
Long story short: The NIS2 Directive represents a significant step forward in strengthening cybersecurity across Europe. It challenges organizations to revisit and enhance their IT security strategies, introducing robust measures to counter the increasing threats in the digital landscape. While the requirements may seem complex – from adapting IT infrastructure to securing supply chains – they provide an opportunity to build stronger systems and secure long-term benefits such as better protection, increased resilience, and a trust advantage with customers and partners.
And you don’t have to do it alone: With our IT security services, we can provide comprehensive support in implementing the NIS2 Directive, helping you close security gaps, minimize risks, and build resilient systems to ensure compliance with NIS2.
Source
NIS 2 Directive Training, Updates, Compliance
NIS-2-Richtlinie - neue gesetzliche Anforderungen zur IT-Sicherheit - IHK Magdeburg
Microsoft Digital Defense Report 2024