Top 5 Ways to Reduce False Positives in Your SOC
Top 5 Ways to Reduce False Positives in Your SOC
One of the biggest challenges Security Operation Center (SOC) teams face is the flood of frequent false alarms, commonly known as false positives. These false positives can overwhelm analysts, divert attention from real threats and lead to alert fatigue. As a result, the SOC's ability to respond quickly and effectively to real threats is weakened. Remember, a SOC is the heart of every organization’s cyber defense. It is playing a critical role in detecting, responding to, and mitigating security threats.
Reducing false alarms not only improves efficiency within the SOC but also helps to detect real threats at an early stage. A streamlined alerting process allows the SOC to focus on critical issues, improving response times and ensuring that real threats are addressed before they can escalate. The more sophisticated and accurate your detection rules are, the better your SOC will perform, saving time and resources and reducing operating costs.
I think everyone who has a SOC has noticed at some point, that a SOC is only as good as the support it receives in developing and refining detection rules. It is one thing to deploy analytic rules and leave them be, but another to actively engage with and improve them over time. Of course, this requires a structured process and consumes more time than the initial deployment, but the benefits far outweigh the effort.
False positives waste time, lead to alert fatigue and, more dangerously, can lead to real threats being overlooked. The more time analysts spend on triaging non-critical alerts (which every false positive should be), the more they lose focus on incidents that truly matter. Reducing false positives is therefore not only essential for improving SOC efficiency but is also critical for strengthening your organization’s overall security posture.
But this is not just a problem for SOC analysts – it affects the entire organization. Excessive false positives can slow response times, increase operational costs, and leave the organization vulnerable to real threats. By refining detection rules and improving the process, the security team can work more effectively, benefiting the organization by ensuring faster and more accurate responses to real incidents.
This article is especially relevant for SOC analysts, security engineers, IT managers as well as CISOs and business leaders who want to ensure their SOC is operating optimally.
Here are five key strategies to help minimize false positives in your SOC:
1. Fine-Tune Detection Rules
As already mentioned, it is good to have a process which will be to regularly review and optimize detection rules. This is one of the most effective ways to reduce false positives. Most of the queries that come out-of-the-box are not fully aligned with your environment and should just be used as a starting point. Spend time identifying and adjusting these rules to really reflect your organization’s needs.
For example, with Microsoft Sentinel you can check the classification of your incidents and try to get your five least accurate analytic rules.
Here is an example in KQL to check how it was classified in your environment:
SecurityIncident
| where TimeGenerated >= ago(30d)
| summarize arg_max(TimeGenerated, *) by IncidentNumber
| summarize
Total = count(),
BenignPositive = countif(Classification == "BenignPositive"),
TruePositive = countif(Classification == "TruePositive"),
FalsePositive = countif(Classification == "FalsePositive") by Title
| extend TruePositiveRate = round(
(TruePositive * 1.00 / (BenignPositive + TruePositive + FalsePositive)),2
)*100
| project-away BenignPositive, TruePositive, FalsePositiveThe result should look like this:
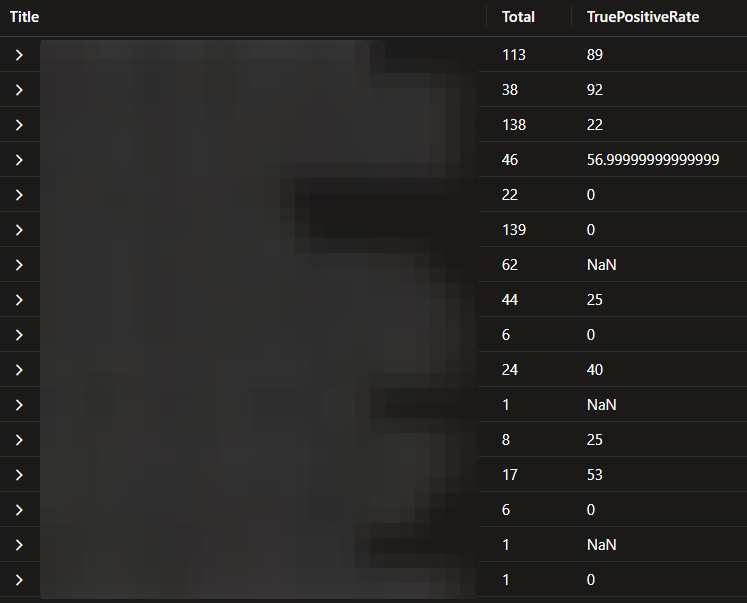
This query uses the table “SecurityIncident” to get all incidents.
The second line is just to receive all events for the last 30 days.
In the third line we get the last information from the incident based on column “IncidentNumber”. Be aware that each update for an incident creates a new entry in “SecurityIncident” table.
From line four to eight we summarize all events based on their title and count events if their classification matches one of these: “BenignPositive”, “Undetermined”, “TruePositive”, “FalsePositive”. Furthermore, we count all events based on title and incidents with no classification at all.
Line nine to eleven we calculate the true positive rate. For this we get all true positives and divide them through all true, false, and benign positives. We do not use the undetermined because these will be set by Defender XDR and can be anything.
In the last line we remove all unnecessary columns we do not need to get the first insights.
With this information you can prioritize which incidents have a low “TruePositiveRate” and should be looked at.
2. Use Threat Intelligence Data to Enrich Alerts
Integrating threat intelligence into your investigation workflow is a powerful way to handling incidents faster and making quicker decisions. By correlating incoming alerts with trusted threat intelligence feeds, you can determine the legitimacy of the threat more accurately and faster.
For instance, using threat intelligence sources like Microsoft Threat Intelligence or third-party feeds (you have heard most likely from VirusTotal) can help you automatically compare suspicious indicators against known bad actors. You could check IP addresses, domains or file hashes and make (semi-)automatic decisions. With this you can even get a better prioritization for real threats.
To get a better understanding I created a schematic view. With the information of entities in your alert you can query multiple sources of information to enrich your initial data.

To dive more into this part, you should get familiar with Logic apps and use them in your Microsoft Sentinel workspace. Get started by reading the following article: Unleash the power of Sentinel - SOAR | water IT Security GmbH (water-security.de)
3. Automate Low-Risk Alerts
A game-changer can be automation when it comes to managing and reducing false positives because not every alert requires a manual review by an analyst. After operating a SOC for some time, there should be several playbooks in place detailing how individual alerts are handled. Identify those where you can have quick wins! Look for actions like closing an incident because it is just there for compliance purposes or known behaviors, escalating it to a specific department or triggering further investigations if certain conditions are met.
This approach ensures that your SOC analysts are not stalled by repetitive and low-value tasks. With this they can focus on incidents that require experience. We could go on and on with the list what you could also automate but that would go beyond the scope of this article.
4. Take Advantage of UEBA
With User and Entity Behavior Analytics (UEBA) you can reduce false positives. SOCs can use this information to understand normal behavior patterns of users and entities within the tenant. Anomalies that do not match regular patterns are flagged for review, which adds context to alerts and help analysts determine if an incident is suspicious or normal activity.
In Microsoft Sentinel you have built-in UEBA features that correlate data from different data sources and automatically enhance detections with user context.
5. Review Your Use Cases
Finally, your detection rules and use cases should never be static. You must review them regularly and update them based on organizations infrastructure changes, new threats or changed business needs. For instance, if your company adopts a new cloud service, a new third-party application or migrates to a hybrid work model, the attack surface changes. That is the moment you must adapt your detection rules to account for new behavior, changed risks or new vulnerabilities.
Conducting periodic review of your detection logic allows you to eliminate outdated rules that no longer apply, generate false positives, and adjust to emerging attack techniques. This ensures that your SOC remains proactive in an ever-changing environment.
Like the DevOps loop shows us, it is a recurring process we should follow to optimize our environment on a regular basis.
Conclusion
False positives will always be a challenge for SOCs, but with the right approach you can significantly reduce their impact. By fine-tuning analytic rules, leveraging threat intelligence, automating low-risk alerts, utilizing UEBA and reviewing your use cases you can create a more efficient SOC that focuses on real threats.
Reducing false positives is not just about improving workflow efficiency, it is about enabling your SOC to work smarter and respond faster, ultimately keeping your organization safe. Now is the time to take action—review your detection rules, refine your processes, and ensure your SOC is operating at its full potential.


