What is Microsoft Entra ID Protection?
Microsoft Entra ID Protection
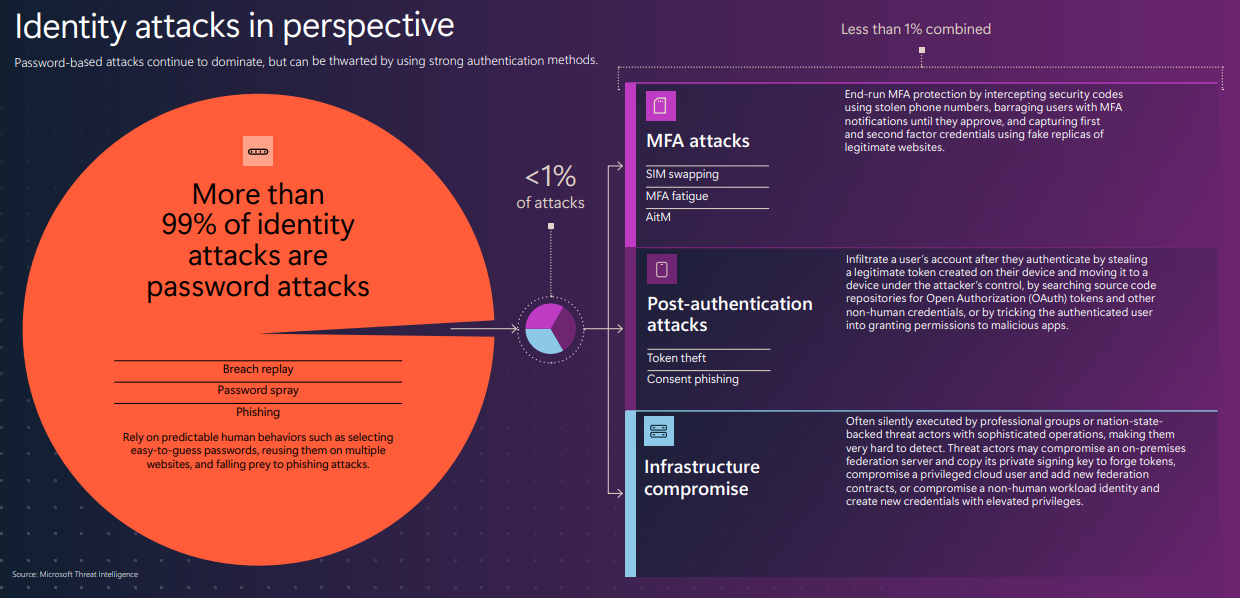
As part of the Microsoft Entra Suite, Entra ID Protection is designed to provide organizations with advanced tools to safeguard identities. The Microsoft Defense Report 2024 reveals a crucial insight: 99% of today’s identity attacks are password-based.
This alarming statistic is largely driven by human behaviors—such as using weak passwords, reusing them across multiple sites, and falling victim to phishing scams. Passwords continue to be a major security vulnerability, and organizations require more than traditional defenses to protect against evolving threats.
Microsoft Entra ID Protection steps in as a comprehensive solution to protect identities and manage the risks tied to identity-based threats. As identity becomes the primary target of cyberattacks—growing in both sophistication and frequency—Entra ID Protection leverages machine learning and advanced analytics to detect and mitigate risks in real time.
How It Works
1. Risk Detection
Entra ID Protection identifies suspicious activities and flags them as risks. These risks are categorized into two types:
- User Risk: Assesses the likelihood that a user account is compromised:
- Leaked credentials detected in public breaches.
- Unusual user behavior indicating account takeover.
- Sign-in Risk: Evaluates the likelihood that a specific authentication attempt is malicious:
- Sign-ins from unfamiliar locations or devices.
- Impossible travel (e.g., a user signs in from two geographically distant locations within a short time).
- Use of anonymous IPs (e.g., VPNs or Tor).
2. Advanced Analytics
Entra ID Protection employs machine learning and AI to analyze:
- User behavior patterns.
- Sign-in activities across Microsoft’s global ecosystem.
- Threat intelligence gathered from billions of signals processed by Microsoft daily.
The system continuously improves by learning from new attack patterns and adapting its risk evaluation models.
3. Risk-Based Policies
Once risks are identified, risk-based Conditional Access policies can be configured to automatically respond to different levels of risk. Examples of automated actions include:
- Requiring Multi-Factor Authentication (MFA) for high-risk sign-ins.
- Blocking access from risky locations or devices.
- Forcing password resets for users flagged as compromised.
These policies allow organizations to balance security and usability by applying stricter measures only when necessary.
4. Automated Remediation
For common scenarios, Entra ID Protection enables automatic remediation to mitigate risks without manual intervention. For instance:
- High-risk user accounts may be prompted to reset their passwords.
- Sign-ins flagged as high-risk can be automatically blocked, preventing potential unauthorized access.
5. Risk Investigation and Reporting
Admins and security teams can access detailed reports and logs through the portal to:
- Investigate flagged risks and analyze trends.
- Gain insights into specific user or sign-in risks.
- Export risk data to external systems like Microsoft Sentinel or third-party SIEM tools for further analysis.
6. Integration with the Microsoft Ecosystem
Entra ID Protection integrates seamlessly with other Microsoft security tools:
- Microsoft Sentinel: For advanced threat hunting and correlation with other security data.
- Defender for Identity: To detect lateral movement and suspicious activity within on-premises environments.
- Defender for Cloud Apps: To enforce real-time session controls based on detected risks.
This integration provides a holistic security approach across cloud and on-premises environments.
7. How Risks are Calculated
Risk detection uses multiple factors to determine the severity of the threat, including:
- Location: Is the sign-in coming from a new or unusual location?
- Device: Is the device registered or compliant with the organization’s policies?
- IP Address: Does the sign-in originate from an anonymous proxy or a known malicious IP?
- Behavior: Is the user's behavior consistent with past activities?
Based on these factors, risks are classified as low, medium, or high, allowing organizations to customize responses accordingly.
However, it’s important to note that these levels reflect Microsoft’s confidence in detecting an attack, not necessarily the severity of the attack itself. This distinction can sometimes lead to misunderstandings about how to respond as an administrator.
| Risk Level | Meaning | Recommended Actions |
| Low | Unusual behavior, but not enough evidence to suggest a serious threat. | Collect data for potential future correlation, monitor trends. |
| Medium | Stronger indicators of suspicious activity. | Require MFA, monitor user activity to reduce risk without major disruptions. |
| High | High confidence of ongoing malicious activity. | Block access, enforce immediate password resets. |
8. Administrator Actions
Admins can take manual actions to investigate and mitigate risks:
- Mark users as safe if flagged risks are determined to be false positives.
- Block or disable accounts showing signs of compromise.
- Require password changes or security reviews for affected accounts.
Scenario: Defending Against a Password Spray Attack
Let’s consider a real-world example of how Entra ID Protection helps defend against a password spray attack. Imagine an attacker tries common passwords across multiple user accounts within Alex's company. Entra ID Protection identifies suspicious login patterns—such as repeated failures from different IPs—and assigns a high-risk level to affected accounts. Depending on the company’s policy, several automated responses might occur:
- Enforce MFA: Users involved in the attack are required to complete MFA for their next login, ensuring unauthorized access is blocked even if a password is compromised.
- Block Access: Temporary access blocks are applied to the highest-risk accounts until users complete a security review.
- Trigger Password Reset: Users are prompted to reset their passwords, ensuring compromised credentials can't be reused.
This rapid detection and automated response minimize the attacker's window of opportunity and keeps the company secure.
The key advantage of Entra ID Protection is the speed and precision with which it can detect and respond to this kind of widespread threat. Automated actions minimize the window of opportunity for the attacker while providing the IT team with the visibility they need to maintain security. By acting early, password spray attacks can be thwarted before any accounts are compromised, drastically reducing the potential impact on the organization.
Key Insights for Admins
- Risk Levels Reflect Confidence, Not Severity: The risk level represents how certain Microsoft is that something unusual or malicious is happening. A low-risk event might still indicate the early stages of an attack, but it’s less certain compared to a high-risk event.
- Policy Recommendations: Microsoft recommends targeting high and medium risks in your Conditional Access policies. This approach minimizes user disruption while still offering robust protection.
- Investigative Use of Low Risks: Low-risk events are ideal for investigation and analysis, especially when aggregated with other signals in tools like Sentinel. However, they are not typically used for setting automated policies because of their higher likelihood of false positives.
Want to gain deeper insights and engage in discussions with experts?
Sign up for our upcoming Entra Suite Roundtable today and secure your spot for exciting conversations and valuable networking opportunities: Roundtable Entra | water IT Security GmbH


