Entra ID Governance
Entra Suite has a product that, in my opinion, is not used as much as it should be: Entra ID Governance.
Just a couple of days ago, I heard from a friend about his frustrating first day at a new job. His User ID was not ready, he was missing access to critical applications, and he couldn’t join the Teams channels he needed to collaborate with his colleagues. This kind of experience is not just annoying, it slows down productivity and creates unnecessary security risks.
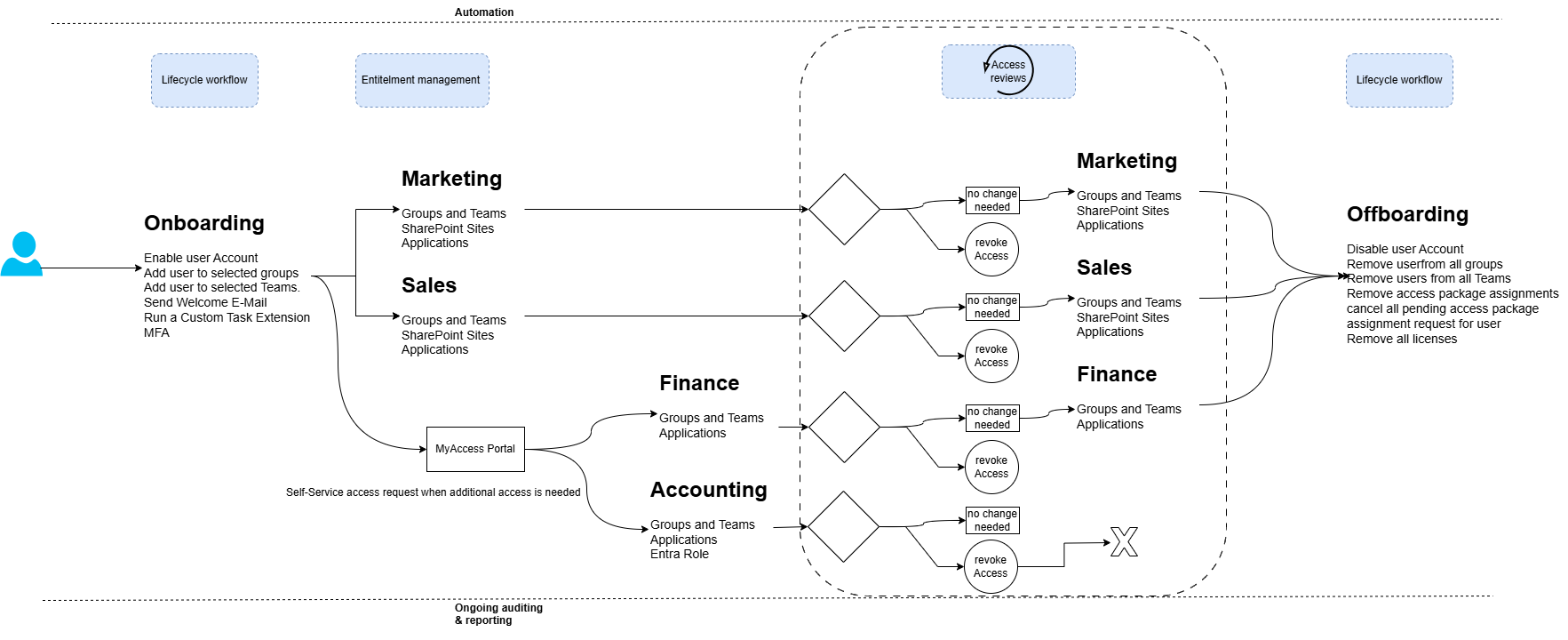
Entra ID Governance is designed to solve these challenges by helping organizations govern and manage access in a structured, automated, and compliant manner. It enables companies to control who has access, when they have access, and why they need access, reducing risks associated with excessive or outdated permissions
Key Features and Benefits
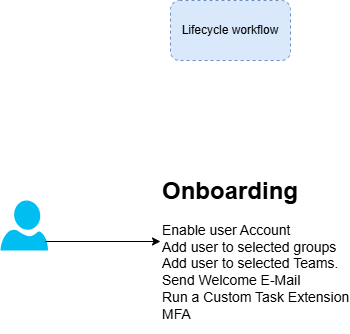
1. Automated Identity Lifecycle Management
Imagine it’s your first day at a new job, and the moment you log in, every tool and app you need is already set up –no frantic calls to the help desk, no waiting for approvals. That’s exactly the experience Automated Identity Lifecycle Management aims to deliver. It ensures new hires hit the ground running and that employees who leave lose access automatically. Plus, Microsoft’s predefined workflow templates make it easy to tailor these processes to your organization, so IT isn’t bogged down with manual account setup. This Automation:
- Ensures that users receive appropriate access when they join an organization and lose access when they leave.
- streamlines provisioning and deprovisioning by leveraging HR and directory data.
- Reduces manual workload on IT teams, freeing them for more strategic tasks.
2. Entitlement Management
We’ve all seen it: trainees or interns start with minimal permissions, but by the end of their training, they’ve somehow accumulated access to half the company’s apps and sites. Without proper governance, those permissions often linger long after they’re needed, creating unnecessary security and compliance risks.
Entitlement Management solves this by automating “access packaging,” ensuring everyone gets exactly what they need–no more, no less–from day one. Think of an access package as a bundled collection of resources (apps, Teams channels, SharePoint sites, etc.) tailored for a specific role. For example, if someone’s job title is “Marketing,” they automatically receive the Marketing package, which includes everything the marketing team typically uses. This eliminates the hassle of manually assigning and removing permissions, and it prevents leftover access from piling up. Benefits include:
- Self-service access requests with approval workflows, ensuring only authorized users gain access.
- Predefined access packages that bundle applications, files, and group memberships for specific roles.
- Just-in-time (JIT) access, preventing standing privileges and minimizing exposure.
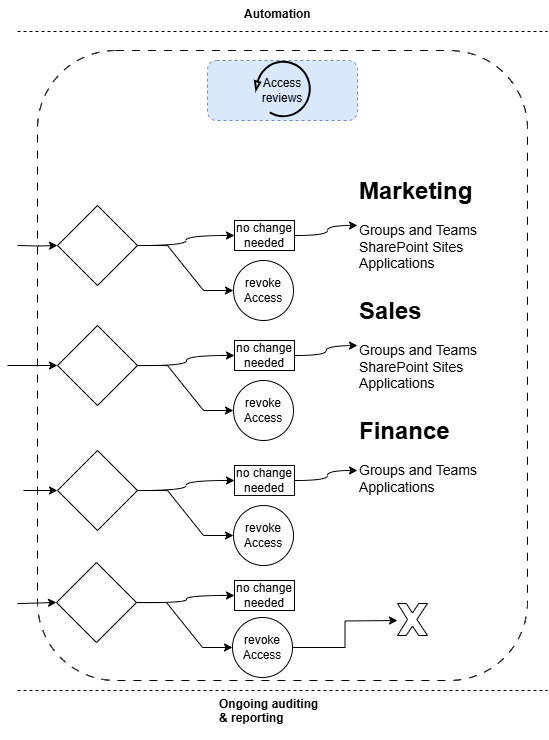
3. Access Reviews and Recertification
Picture this: a project wrapped up months ago, but you’re still unsure which users–internal or external–still have access to the data or Teams channels linked to it. That’s where Access Reviews come in. They help you periodically check who really needs ongoing access to specific apps, groups, or resources. If someone’s moved on, you can revoke their permissions in a click, keeping your environment clutter-free and secure.
I’d suggest running these reviews at least for guest users and for groups excluded from Conditional Access policies. This ensures external collaborators don’t hang onto access forever and that your main security controls aren’t accidentally bypassed. Through periodic access reviews:
- Managers and security teams can validate user access based on real-time needs.
- Inactive accounts and unnecessary permissions are promptly revoked.
- AI-powered recommendations help streamline the process, reducing review fatigue.
4. Privileged Identity Management (PIM)
We’ve all witnessed those “uh-oh” moments when someone leaves the IT team or changes roles, but their high-level admin rights remain intact. It’s a classic recipe for security risks and audit nightmares. Privileged Identity Management (PIM) prevents these slip-ups by tightly controlling who holds privileged roles, and for how long. Think of it as a safety net that ensures sensitive permissions are only active when absolutely necessary—no lingering “god-mode” accounts to worry about. Benefits:
- Users only get privileged rights for the exact window they need, reducing the chance of misuse.
- Elevating privileges often requires a manager or security team’s approval, adding a critical oversight measure.
- PIM offers real-time visibility into who has admin permissions, making audits simpler and reducing risk.
- Every privileged action is recorded, so you can quickly detect unusual behavior or compliance gaps.
5. Actionable Reports and Insights
Even with the best governance in place, it’s impossible to make good decisions without understanding the real-time status of your environment. Actionable Reports and Insights give you the data you need to spot suspicious behavior, verify policy effectiveness, and streamline compliance tasks—all at a glance. Benefits:
- Dashboards visualize key metrics, so you can instantly see where risks or inefficiencies lie.
- Advanced analytics highlight trends and anomalies, helping you focus on genuine threats and optimization opportunities.
- Exportable reports simplify audits, saving both time and stress when demonstrating compliance.
- Real-time alerts keep your security teams ahead of potential issues, letting them act before problems escalate.
Entra ID Governance is all about keeping access simple, secure, and stress-free. You no longer have to chase after approvals or worry about forgotten guest accounts lurking in the system. Instead, everything—from assigning roles to running security checks–happens automatically in the background. New hires can jump in on day one without waiting around for someone to give them the right permissions, and managers can sleep easier knowing nobody has leftover access to sensitive data.
- No More Manual Work: Automated workflows handle the heavy lifting behind the scenes.
- Reduced Security Risks: Stale accounts and over-permissioned users become a thing of the past.
- Better User Experience: Onboarding and access requests happen smoothly, so people can focus on work instead of IT hurdles.
- Straightforward Compliance: Consistent policies and clear audit trails mean you’re covered when it’s time to prove your security posture.
By blending automation, AI-driven insights, and a Zero Trust philosophy, Entra ID Governance helps you strike that perfect balance between strong security and effortless productivity. It’s essentially a smarter, friendlier way to manage who gets in (and who doesn’t), without tying everyone up in red tape.