Wiper-Malware (Part 2)
Wiper was already explained in more detail in Wiper ransomware (Part 1). However, here is a brief summary. Wiper is ransomware that pursues destruction as its goal. For example, it deletes the MBR, MFT, overwrites the files or encrypts the files and destroys the decrypt key.
Attacks
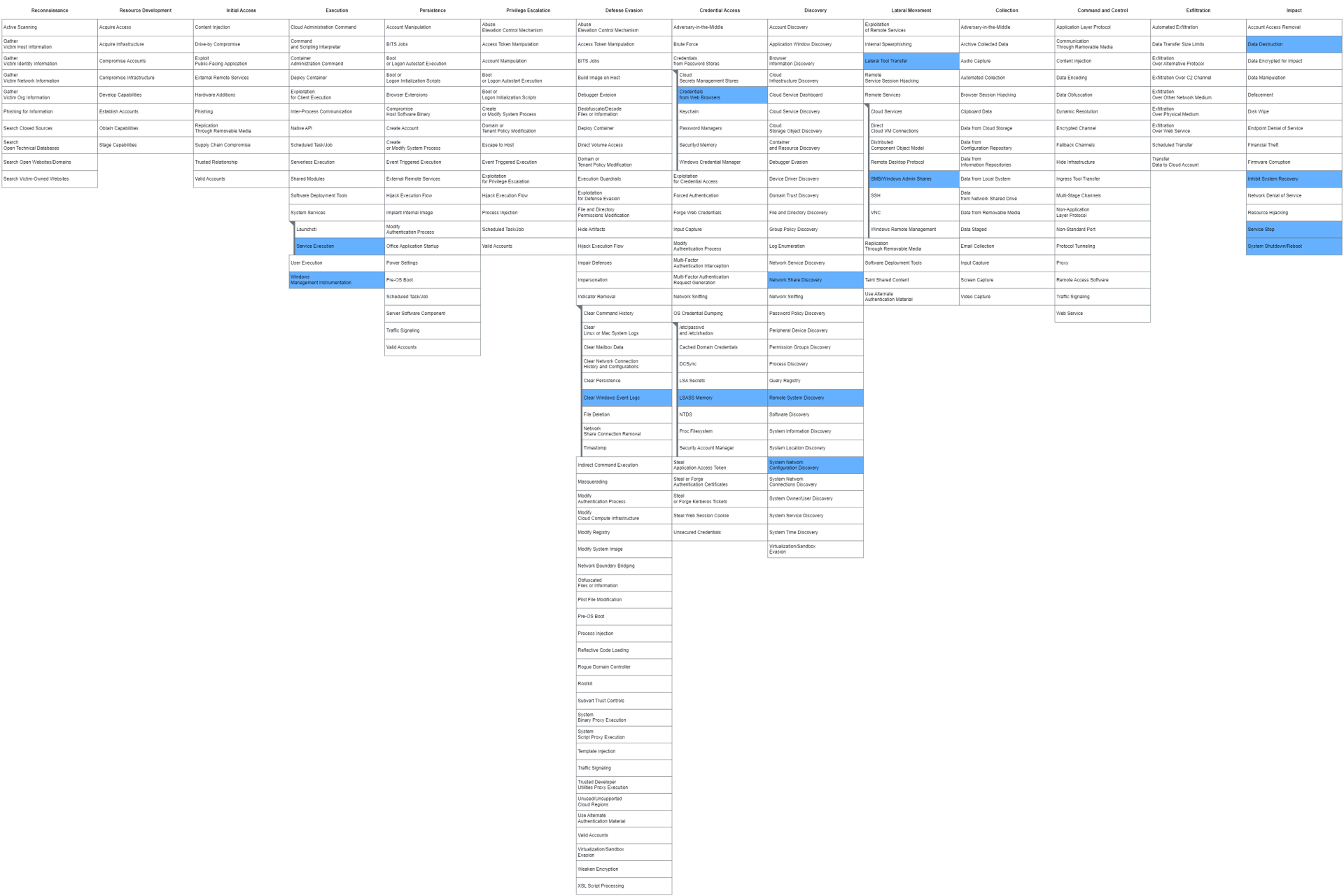
Wiper Malware Timeline - https://www.fortinet.com/blog/threat-research/the-year-of-the-wiper
In addition to crucial wipers such as NotPetya, wipers such as Olympic Destroyer, which shows that the actors are not only targeting companies but also public events, and GermanWiper, which not only destroys data but also extorts ransom money with it and thus deviates from the typical pattern, as well as some other wipers have appeared on the scene in recent years.
GermanWiper/Ordinypt 2019
At the beginning of November 2017 and the end of July 2019, several German companies received phishing emails that looked like legitimate applications. These contained the data “<Name>_Bewerbungsfoto[.]jpg” or “<Name>-Bewerbungsfoto[.]jpg”, as well as a ZIP file called “Unterlagen_<Name>[.]zip” or “<Name>-Bewerbungsunterlagen[.]zip”. These ZIP files contain an LNK shortcut file that installs Ordinypt Ordinypt or GermanWiper. The malware is known under the name Win32[.]Trojan-Ransom[.]Ordinypt[.]A.
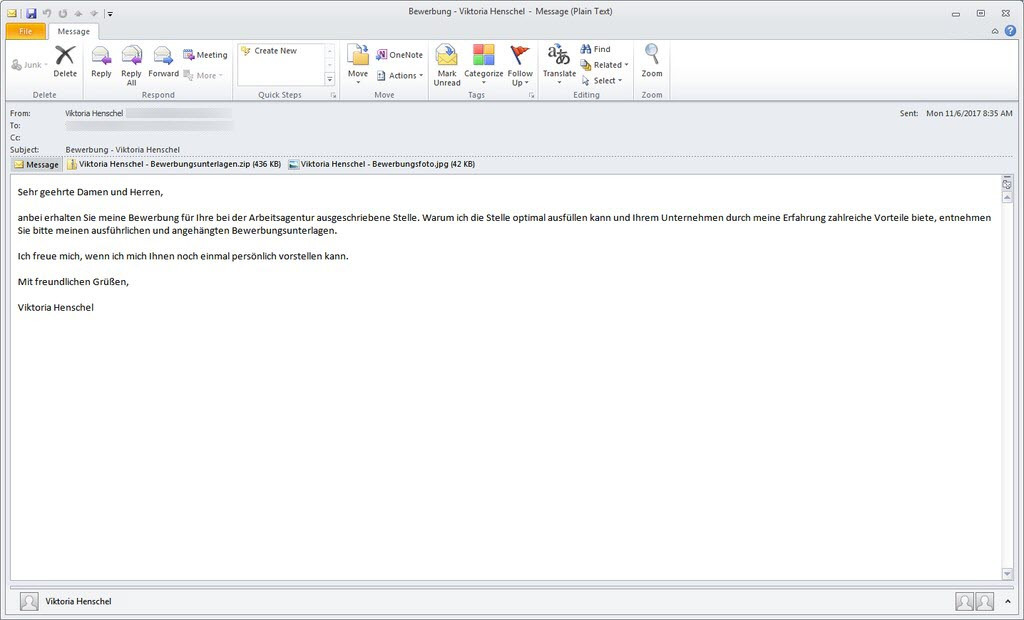
2017 Phishing-Mail (Ordinypt) - https://www.gdata.de/blog/2017/11/30151-ordinypt
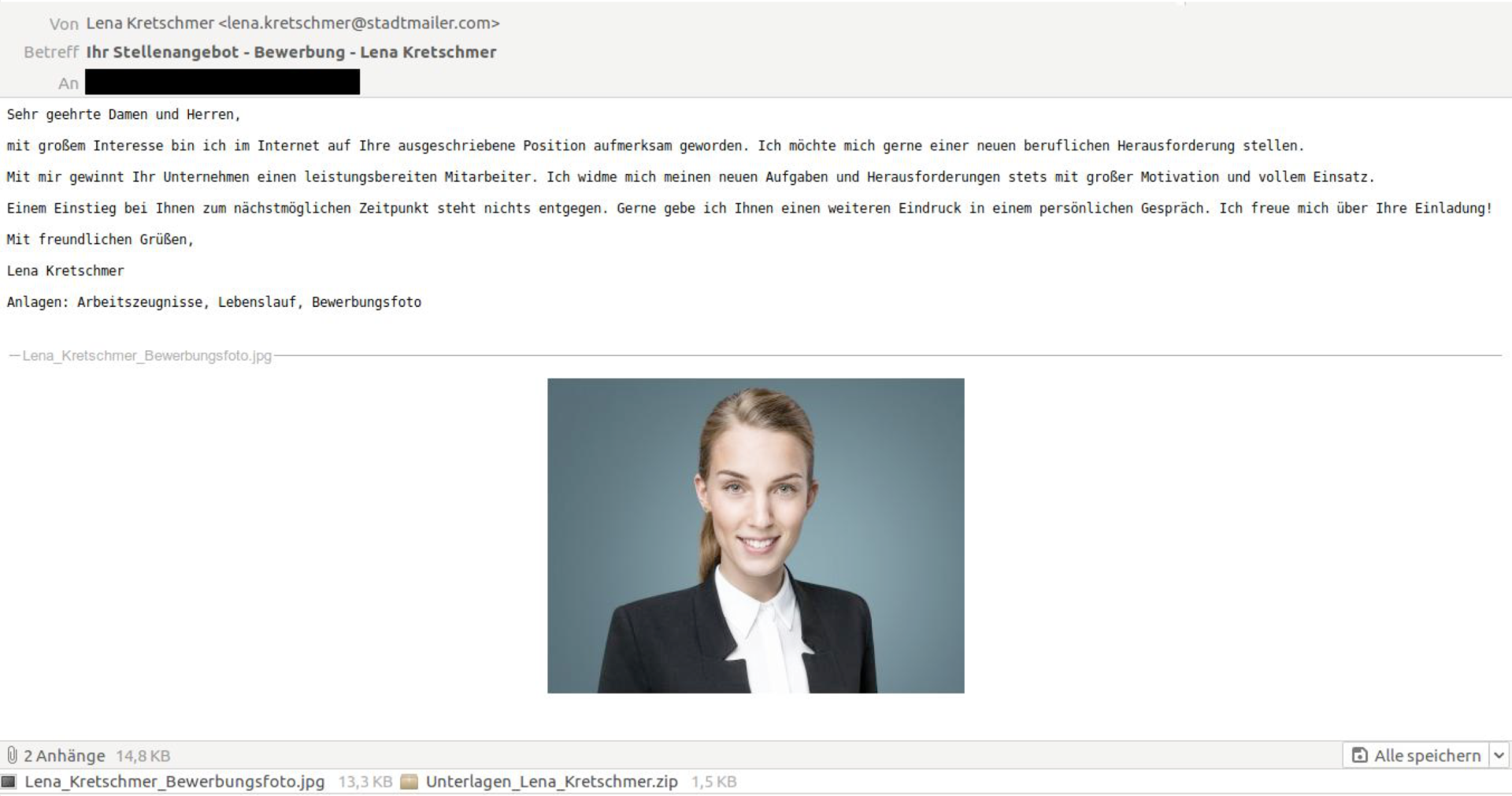
2019 Phishing-Mail (GermanWiper) - https://x.com/certbund/status/1157246114678169600/photo/1
If the GermanWiper is installed, it overwrites the data with 0x00 bytes and a random extension such as [.]08kJA. The name of the data is chosen at random. It can be assumed that the same procedure was used with Ordinypt.

Random name of encrypted files - https://www.gdata.de/blog/2017/11/30151-ordinypt
If the data has been encrypted, the file “Wo_sind_meine_Dateien” also appears, in which the blackmail email can be found. This message states that all data has been encrypted, that a special decrypt key is required to decrypt it again, that exactly 0.12 Bitcoin (approx. 600€) is to be transferred, how Bitcoins can be obtained, as well as a piece of program code that generates a new Bitcoin address for each email. In addition, this Bitcoin is to be transferred within 7 days. The blackmail message also states that the data was encrypted with a 256-bit AES algorithm at military grade.
It is striking that the message from Ordinypt and GermanWiper was both written in very good German and no spelling mistakes are recognizable.
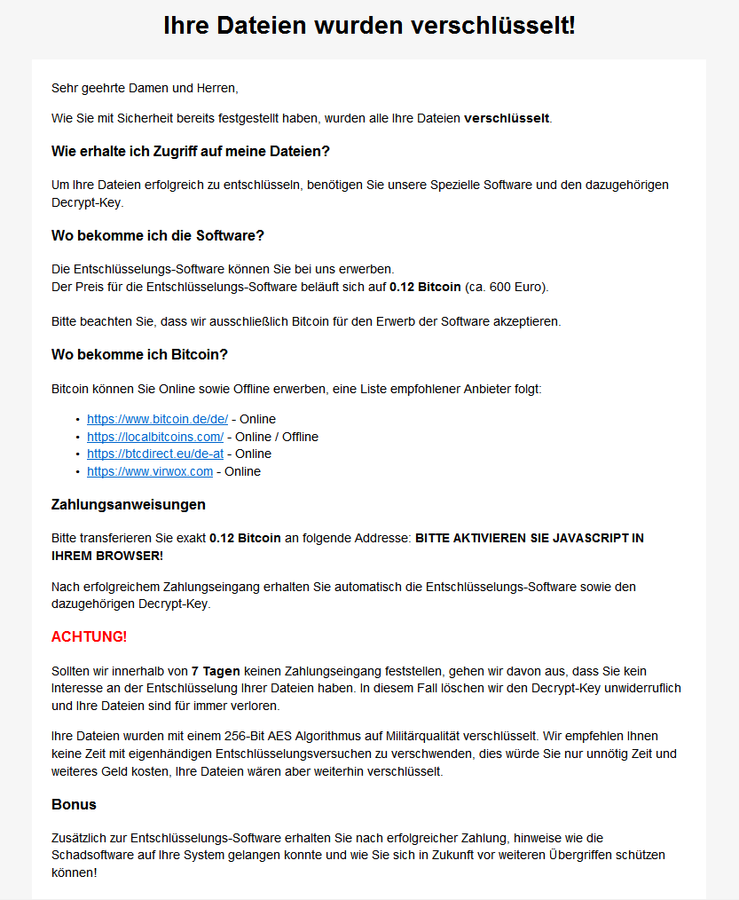
Ordinypt blackmail - https://www.gdata.de/blog/2017/11/30151-ordinypt
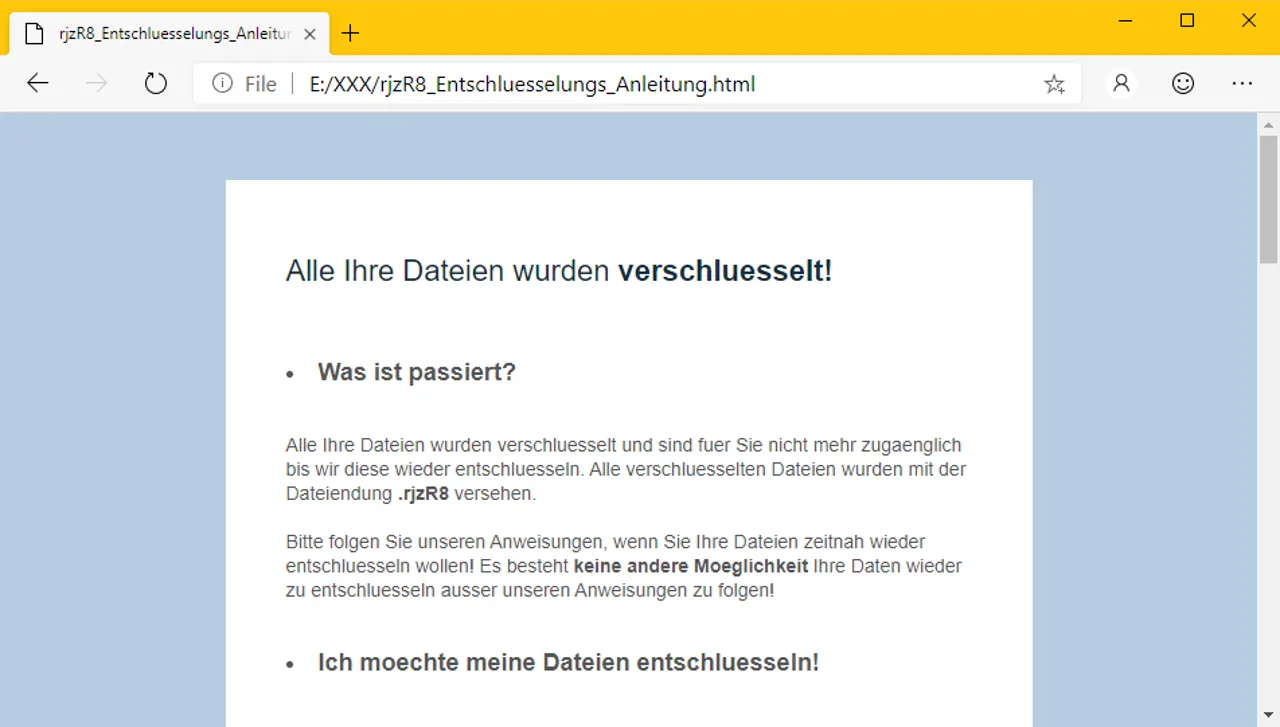
If the ransom was paid and the decrypt key received, Ordinypt was able to determine that the data is much smaller. As can be seen in the screenshot, a file with 841 MB is now only 7.66 MB in size. This underlines the theory that Ordinypt also overwrote the data with 0x00 bytes.
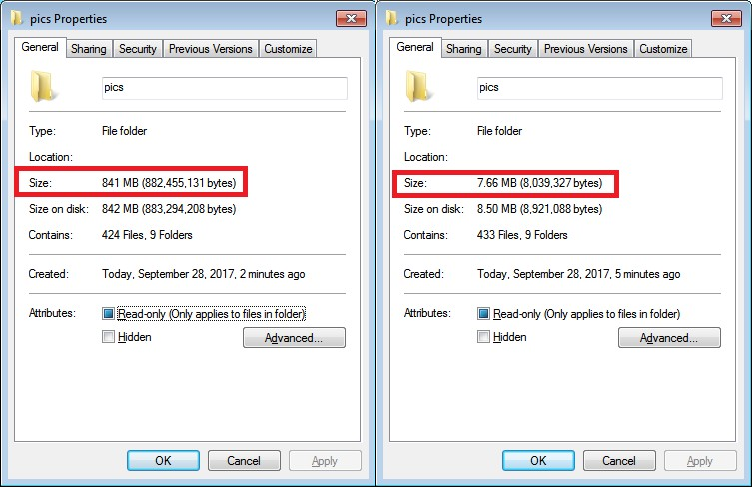
Size of encrypted data - folders are almost empty - https://www.gdata.de/blog/2017/11/30151-ordinypt
In general, the data was encrypted here and the decryption key was not destroyed, which indicates normal ransomware. However, since the data was overwritten, it is still a wiper, even though it was encrypted and blackmailed.
Here you can find a Yara rule that checks typical hashes, strings, etc.

Olympic Destroyer 2018
On February 11, 2018, Olympic Destroyer (S0365) aka Sourgrapes was used to disrupt the South Korean Winter Olympics ceremony in Pyeongchang, presumably in retaliation for Russia's doping ban. According to the organizers, technical problems arose but did not affect any critical systems.
Olympic Destroyer - https://securityaffairs.com/70014/apt/olympic-destroyer-attribution.html
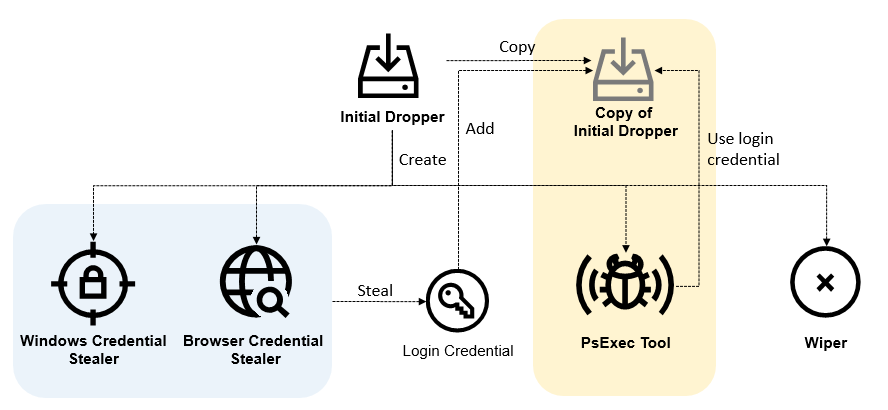
The attack begins with an initial dropper that is injected into a system and drops and executes other components of the attack.
Next, credentials are executed by a Windows or browser credential stealer, for example. The Windows credential stealer extracts credentials that are stored in the Windows system, in particular from the LSASS process (Local Security Authority Subsystem Service).
The browser credential stealer steals login credentials stored in web browsers such as Chrome, Firefox or Internet Explorer. These credentials are collected in a database and used to perform lateral movements around the system to cause further damage. In addition to the lateral movements, the credentials are further abused to use the PsExec tool, which is a Microsoft tool. This is used for legitimate administrative purposes, which is used to execute commands on remote systems. In this case, it is misused to spread the malicious code to other systems.
Next, the initial dropper creates a copy of itself, which spreads to the compromised system in order to carry out the attack and execute the next stage. Finally, the Olympic Destroyer wiper is deployed. Depending on the size of the file, the wiper overwrote it with 0x00 bytes or with uninitialized data. In addition, shadow copies (backup copies of system files), backup catalogs and Windows system and security logs were deleted and the Windows repair console and system services were switched off or deactivated.
A helpful Yara rule, which searches for hashes, commands that are used, for example, to delete shadow copies, and strings that are typical for the Olympic Destroyer, can be found here.

Olympic Destroyer Mitre Att&ck Framework
Dustman 2019
Like Shamoon, Dustman aka BAPCO was mainly used in the oil and gas sector. One of these attacks was on December 29, 2019 against The Bahrain Petroleum Company (BAPCO), which is active in this industry. It is suspected that this attack was carried out on behalf of the Iranian government, possibly to demonstrate its vulnerability. Another assumption is that this is connected to the ZeroCleare Wiper. The similarity between ZeroCleare and Dustman supports this theory.
It is striking that there have been several activities between Iran and Bahrain over the years. One example of this is an attack on Bahrain by APT33, an Iranian hacker group.
In order to gain access to the BAPCO system, the hacker group exploited a VPN vulnerability, which gave them access to login credentials. Due to this vulnerability, which became known in July 2019, the attackers were able to install and execute the malware. This suggests that the attackers had already been in the system since around July 2019.
The next step was to load Dustman into the central antivirus software, which is why this wiper was distributed to all BAPCO computers. Dustman was unable to run properly on some computers, leaving them unharmed and leaving traces of the attackers and the malware.
If the malware was executed on an infected computer, the VPN logs were deleted.

Dustman consists of two main components.
A Dustman[.]exe, which is a Turla Driver Loader binary file, is responsible for loading an EldoS RawDisk driver and other drivers. This RawDisk was already used in Shamoon and is used to interact with files, hard disks and partitions and thus enables e.g. changes to data on hard disks of a local PC. In this case, it was adapted to bypass the Windows x64 Driver Signature Enforcement (DSE), and drivers such as the EldoS RawDisk driver can be installed. This DSE prevents the loading of drivers that do not contain a Windows signature. In this case, a vulnerable VirtualBox version with a Windows signature was used, a shellcode is executed and other drivers can be loaded.
An Agent[.]exe that performs the disk wipe. If the unsigned EldoS RawDisk driver (elrawdsk[.]sys) has been loaded, the wiper binary agent[.]exe is now saved and executed. Thanks to the EldoS RawDisk driver, agent[.]exe can now directly access and erase the hard disk and therefore does not behave like a typical wiper
This Yara rule, which searches for Dustman, checks, among other things, the hash or typical byte sequences that are typical for Dustman.

Please note that this is a Yara rule with version v0.6.0. This can lead to problems due to significant changes in Yara version 3.
ZeroCleare 2020
ZeroCleare is a wiper with similarities to Shamoon. ZeroCleare is primarily targeting the energy sector, such as the oil and gas sector, in the Middle East. X-Force IRIS (IBM) suspects that APT34 aka OilRig has gained access to the system.

ZeroCleare - https://securityintelligence.com/posts/new-destructive-wiper-zerocleare-targets-energy-sector-in-the-middle-east/mhsrc=ibmsearch_a&mhq=%26ldquo%3BZeroCleare%26CloseCurlyDoubleQuote%3B%20Targets%20Energy%20Sector%20in%20the%20Middle%20East
Unfortunately, it is unclear how the attackers were able to get into the system, but as with Dustman and Shamoon, the modified Turla Driver Loader (soy[.]exe) was used to bypass Windows x64 Driver Signature Enforcement (DSE). It is striking that the same license key was used for Dustman and ZeroCleare. This modification involves using a vulnerable VirtualBox driver (sadddrv[.]sys) to bypass the Windows signature check, and other drivers can be loaded via shell code executed at kernel level. However, this only works with the 64-bit version, as the procedure is different for the 32-bit version.
Once the various drivers, including the EldoS RawDisk driver, have been loaded, ClientUpdate[.]exe starts the wipe process. This overwrites the MBR and the Windows hard disk partitions. It is unclear when the first ZeroCleare attacks began, with various sources referring to 2019 and others to 2020.
This Yara rule can help to detect ZeroClear in the system, as it checks for known ZeroClear hashes and strings.

Please note that this is a Yara rule with version v0.6.0. This can lead to problems due to significant changes in Yara version 3.
For further research
https://nordvpn.com/de/blog/wiper-malware/
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-malware/what-is-wiper-malware/
https://www.fortinet.com/blog/threat-research/the-increasing-wiper-malware-threat
GermanWiper
https://www.zdnet.com/article/germanwiper-ransomware-hits-germany-hard-destroys-files-asks-for-ransom/
https://www.gdata.de/blog/2017/11/30151-ordinypt
https://x.com/certbund/status/1157246114678169600/photo/1
https://github.com/fboldewin/YARA-rules/blob/master/Ransomware.Germanwiper.yar
Olympic Destroyer
https://github.com/Neo23x0/signature-base/blob/master/yara/apt_olympic_destroyer.yar
https://github.com/Neo23x0/signature-base/blob/master/LICENSE
https://blog.talosintelligence.com/olympic-destroyer/
https://malpedia.caad.fkie.fraunhofer.de/details/win.olympic_destroyer
https://securityaffairs.com/70014/apt/olympic-destroyer-attribution.html
ZeroCleare
https://securityintelligence.com/posts/new-destructive-wiper-zerocleare-targets-energy-sector-in-the-middle-east/?mhsrc=ibmsearch_a&mhq=%26ldquo%3BZeroCleare%26CloseCurlyDoubleQuote%3B%20Targets%20Energy%20Sector%20in%20the%20Middle%20East
https://www.trendmicro.com/vinfo/us/threat-encyclopedia/malware/trojan.win64.zerocleare.a
https://malpedia.caad.fkie.fraunhofer.de/details/win.zerocleare
Dustman
https://malpedia.caad.fkie.fraunhofer.de/details/win.dustman
https://eurepoc.eu/wp-content/uploads/2023/07/Ma_C_Is_BAPCO_final_5f0978930b.pdf
https://exchange.xforce.ibmcloud.com/collection/Comparative-Analysis-of-New-ZeroCleare-Variant-Dustman-4ebc0178fc3440b1a777b3a6b5520528