Wiper-Malware (Part 1)
In the course of researching other Russian state-sponsored hacker groups, I noticed that they often use wipers. Especially since February 24, 2022, the beginning of the war in Ukraine, it is noticeable that several wipers have been used within a very short period of time. This research sparked my interest in the area of wiper ransomware.
A wiper is a ransomware whose main function is wiping, i.e. deleting or overwriting data, damaging the MBR (Master Boot Record) or MFT (Mater File Table). Another task is to encrypt the files.
• When overwriting, which is most commonly used with a wiper, the contents of the file are overwritten with NULL or random bytes, for example.
• With MBR, only the boot process is damaged, which means that all data is still present on the hard disk and will not be lost in the near future.
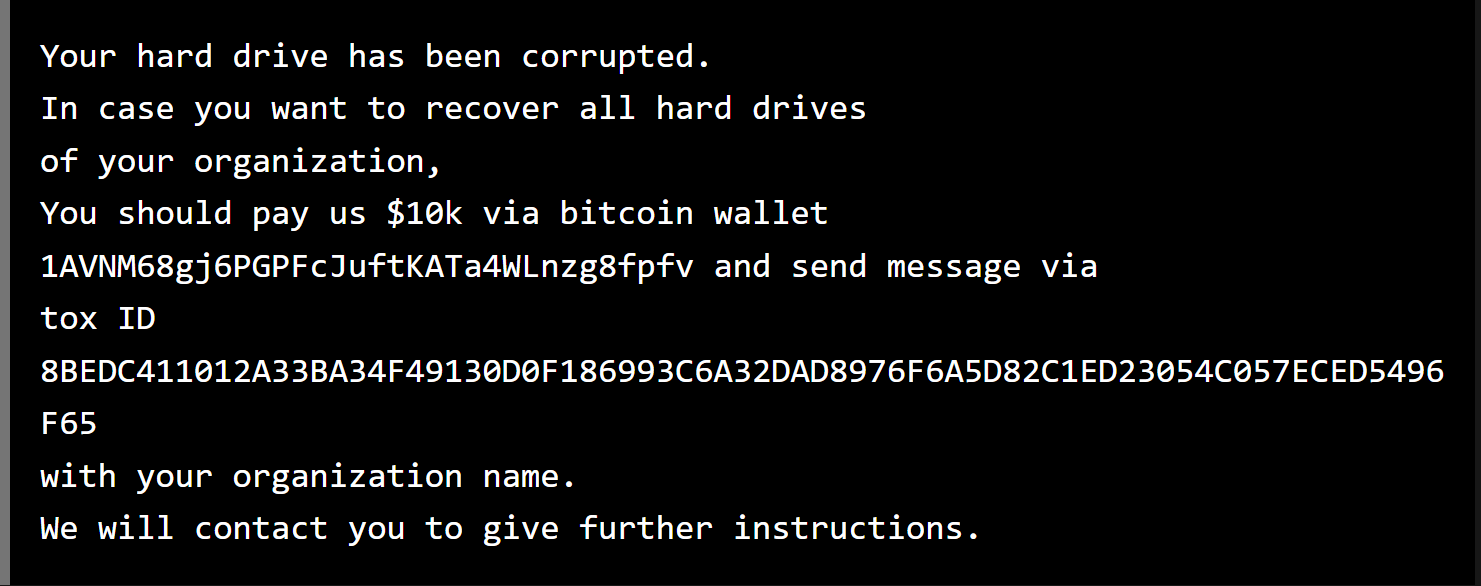
• With MFT, the index that shows where the files are stored on the computer is corrupted. As with MBR, the data is not lost and can be recovered afterwards.
• A wiper can mimic ransomware, encrypting the files and destroying the original version of them. The difference to ransomware, whose goal is encryption and extortion for ransomware payment, is that the decryption key is destroyed.
Wipers are generally not very common, as most attackers target ransomware and direct extortion. What is noticeable is that in recent years they have been used mainly by Russian actors such as Sandworm and, according to the Microsoft Hybrid War Urkaine paper and the Microsoft Digital Defense Report, their use has increased noticeably and was used several times in 2022 and 2023. This actor has been using wipers such as WhisperKill, WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, DoubleZero, Nikowiper.
Nikowiper.mbr and AcidRain or AcidPour since February 24, 2024.
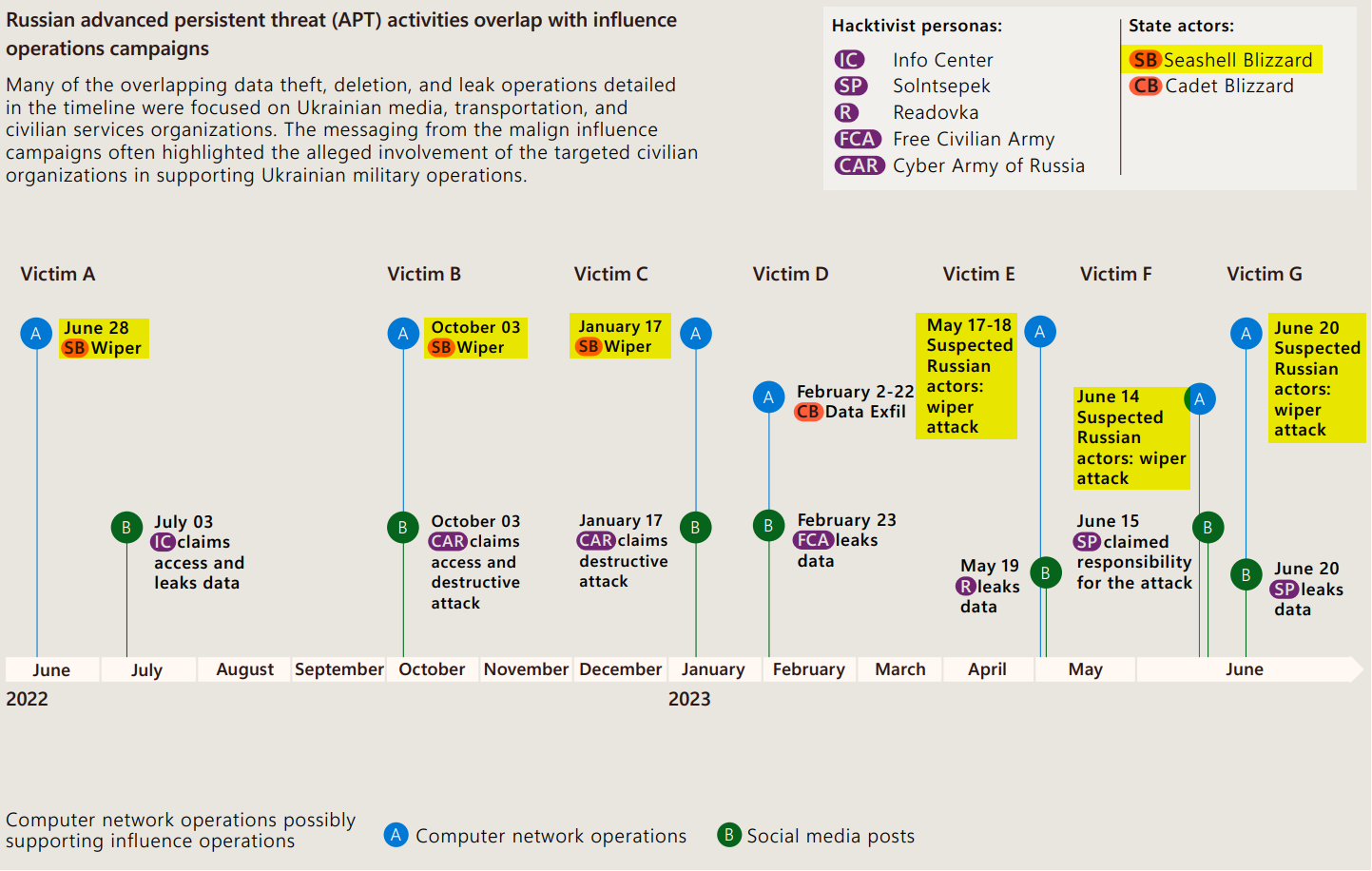
https://www.microsoft.com/en-us/security/security-insider/microsoft-digital-defense-report-2023
Attacks
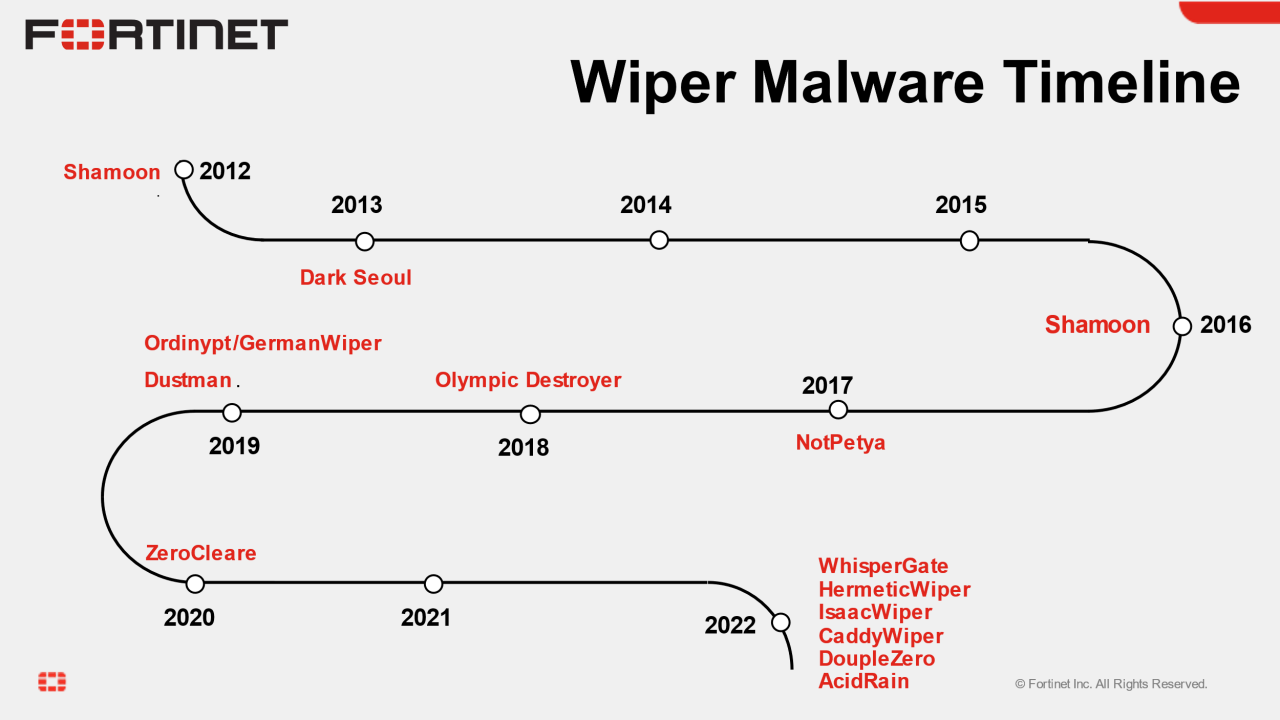
https://www.fortinet.com/blog/threat-research/the-year-of-the-wiper
Over the years, there have been several different wiper attacks which, for various reasons, were primarily aimed at destroying data. One of the first wipers was Shamoon, but it has undergone constant development and is already in its third version. NotPetya also made big waves in 2017, particularly in the media, due to its scope.
Shamoon
One of these wipers is Shamoon (S0140) aka Disttrack, whose main task is to overwrite and infect the Master Boot Record (MBR). McAfee can attribute Shamoon to the threat actor APT33, an Iranian hacker group that targets the U.S., Saudi Arabia and South Korea. The name was found in the path “C:\Shamoon\ArabianGulf\wiper\release\wiper[.]pdb” of the debugging code on the infected computer and was adopted.In the 2010s, a total of three versions of Shamoon were deployed.
Shamoon 1
Shamoon's first version was discovered in 2012 in at least the Saudi Arabian companies “Saudi Aramco” and “RasGas”. Shamoon deleted the MBR and replaced it with images of a burning US flag. This malware contains a module with the string “C:ShamoonArabianGulfwiperreleasewiper.pdb” and is a 900KB PE file containing a number of encrypted resources. These strings can be used for detections to identify Shamoon.
https://securelist.com/shamoon-the-wiper-copycats-at-work/57854/
Shamoon 2
Over the years, other Shamoon versions have developed, such as Shamoon 2, which was used in 2016 to attack the Saudi Arabian organization “Saudi Aramco”, as well as other oil and gas companies, government and KRITIS. In Shamoon 2, the MBR was deleted and replaced by a photo showing the body of Alan Kurdi. Alan Kurdi is a three-year-old Syrian refugee who drowned in the Mediterranean in 2015. The malware was triggered in the evening on November 17, 2016, local time.
Here you will find Yara-Rules, which are helpful for detecting Shamoon 2.

Shamoon 3
Part 1:
Shamoon 3, another version that appeared in 2018, attacked the Italian oil and gas service provider “Saipern”. It affected 300 to 400 servers in the Middle East, as well as some devices in India and Scotland. Shamoon 3 contains Trojan[.]Filerase, another deletion malware, which itself overwrites data on the target system, while Shamoon itself deletes the MBR.
In order for Shamoon 3 to get into the system, the system is usually infiltrated by phishing emails and an installer distributes the malware, which differs depending on the version. MaintenanceSrv32[.]exe is used for 32-bit systems, MaintenaceSrv64[.]exe for 64-bit systems. In parallel, data about the system (regarding the network and configurations) is collected by Memdump, which is later transmitted via C2 communication.
Part 2:
Once the malware has been successfully installed, the connection to the C2 server is established and the data collected by Memdump is transmitted. In addition to transmitting the collected data, this connection is also required to receive and send further information. In addition, a random executable file (%System%{random}[.]exe) is installed, which serves as a network communicator.
Part 3:
The wiper component (%System%{random}[.]exe) is now executed. This component places a .pnf file, which contains important information about the configuration of the attack, in a specific Windows directory, such as %Windows%\inf\. Next, the partition type of the hard disk is identified to find out the best way to overwrite it. The malware sets the system date to August 2012, as the temporary EldoS RawDisk driver license is only valid for this date. This RawDisk is used to interact with files, hard disks and partitions and thus enables e.g. changes to data on hard disks of a local PC.
Part 4:
Now the deletion process can be activated by the malware. If the system date were not changed, this deletion process would be blocked. During the deletion process, critical files are encrypted and the MBR is overwritten, which is why the system can no longer boot. In addition, a special driver, %Windows%\hdv_725x[.]sys, is used to access the hard disk sectors and perform the deletion operations. This driver allows the malware to directly access the memory areas of the hard disks and completely overwrite them.
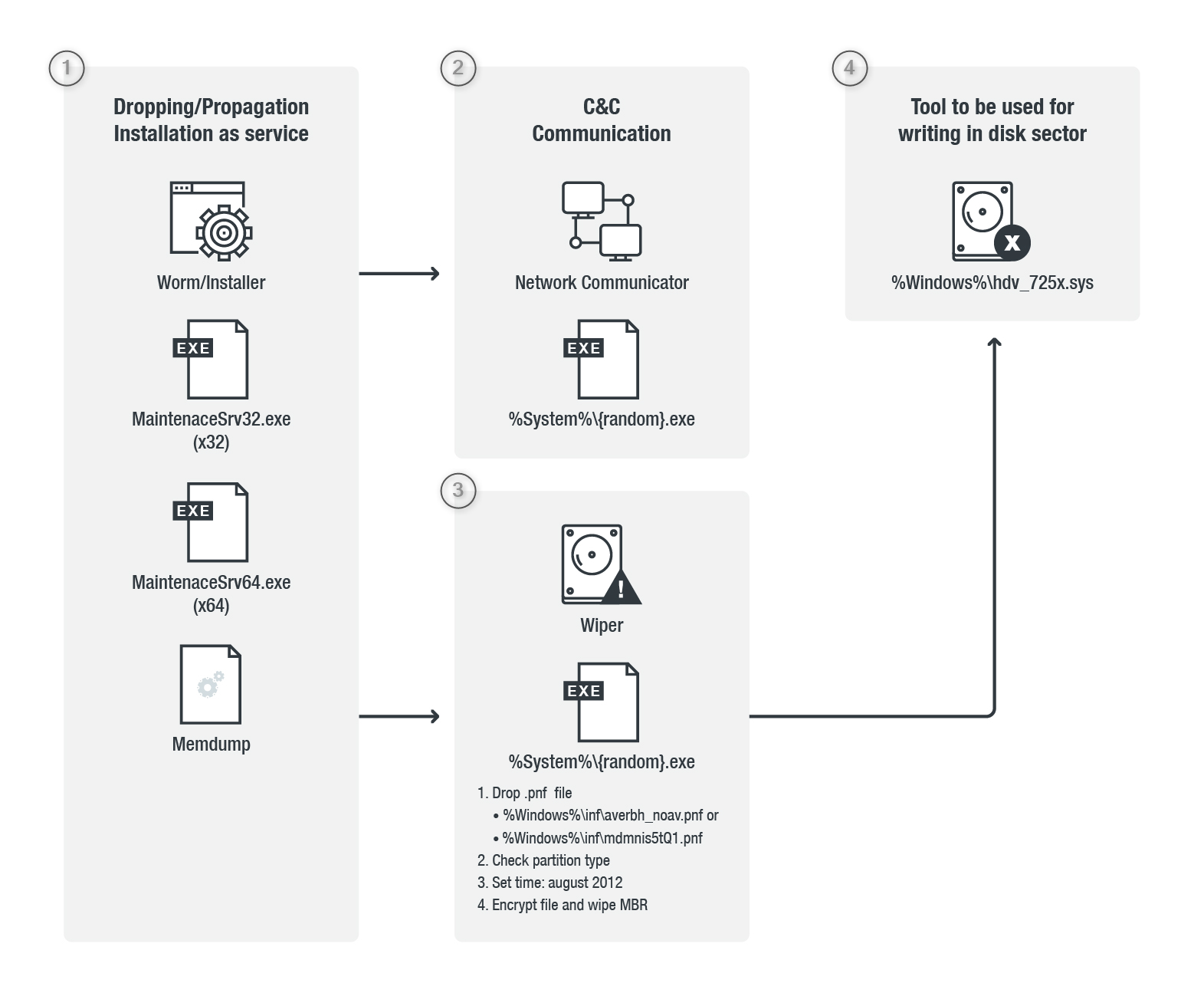
Shamoon Mitre Att&ck Framework
DarkSeoul 2013
In 2013, DarkSeoul became known for an attack on the South Korean media and financial sector that affected approximately 45,000 to 50,000 computers. On March 20, 2013 at 2 pm KST (UTC+9), several media outlets reported outages. The three largest Korean TV stations, KBS, MBC and YTC, as well as the Korean banks Jeju, Nonghyub, Shinhan and Worri, were particularly affected. All companies experienced outages such as network outages at the TV stations, as well as outages in the area of ATMs, payment terminals and mobile banking services.
The attackers were presumably able to gain access to the systems through the AhnLab patch management software, which was used by several affected companies. Apparently, the attackers had access to AhnLab based on stolen legitimate login credentials.Another assumption as to how the hackers got into the system is that on March 19, 2013, a victim received a spear phishing email containing a malicious HTML archive.
It was noticeable that the remote access Trojan 3Rat was installed on several systems. It is suspected that this Trojan had already granted the attackers access to the systems for months in advance and that they were able to compromise victims who were not using AhnLab.
When the attacks were analyzed, it became apparent that at least three dropper variants, at least three Windows wiper variants and a wiper shell script intended for Unix systems were used. Some of these wipers had settings that targeted direct deletion after activation. Some had specific times, such as March 20, 2013 at 2pm KST or March 20 {any year} at 3pm KST. Additionally, the droppers and wipers also differ in whether an attempt was made to disable the antivirus software
DarkSeoul wiped the master boot record (MBR), as well as other files. As with Shamoon, a specific time has been hardcoded into the code and is applicable to different operating systems, resulting in high compatibility. In this attack, it mainly affected Windows and Unix-like operating systems. When the organization attempted a reboot, they found that the operating system was corrupted and the hard drive appeared to be empty.Noevetta is believed that North Korea is behind the attack.
In addition to the attacks on the South Korean media and financial sector, DarkSeoul was also used to attack Sony Pictures Entertainment in 2014 as “Operation Blockbuster by Novetta”. The “Operation Blockbuster” was carried out by the well-known North Korean state-sponsored hacker group “Lazarus”. The DarkSeoul Wiper was also used in this operation along with other malware. This suggests that Lazarus were also involved in the attack on the South Korean media and financial sector.
At the bottom of the text you can find different Yara rules for DarkSeoul. These have been divided into “DarkSeoul_Obf_ChopString : Backdoor”, “DarkSeoul_Obf_BCSUB : Backdoor”, “DarkSeoul_Obf_XORA7 : Backdoor”, “DarkSeoul_Obf_Caracachs : Backdoor”, “DarkSeoul_Keystrings : Backdoor” and “DarkSeoul_Keystrings : Backdoor”

NotPetya 2017
NotPetya (S0368) is a malware that is believed to be used only by Voodoo Bear, a Russian state-sponsored hacking group, and was the cause of a worldwide attack on 27.06.2017 that infected around 2,000 organizations within a few days, but should not be confused with Petya.
Petya is a strain of ransomware that encrypts the victim's Master File Table (MFT) and extorts payment in Bitcoin. Petya first appeared in 2016 and spreads mainly via email attachments, such as a seemingly genuine application containing an infected Dropbox link or a malicious file in disguise.
NotPetya and Petya, which are both wipers, have some other overlaps, which is why they are often confused or seen as aliases. For example, NotPetya also encrypts the entire hard disk, but the difference is that it encrypts the hard disk directly rather than the MFT. NotPetya spreads mainly through various vulnerabilities and credential theft methods. The goal of NotPetya is destruction.
One of these vulnerabilities is EternalBlue (CVE-2017-0144), which was already exploited a month earlier by the WannaCry attack. Despite an update released by Microsoft in March 2017, first WannaCry and then NotPetya had great success in exploiting this vulnerability. Due to faulty updates, EternalBlue is still being exploited.

NotPetya Mitre Att&ck Framework
Further Attacks
Other wipers such as GermanWiper and Ordinypt, Olympic Destroyer, Dustman and ZeroCleare will be looked at in more detail in Part 2.
For further research
https://nordvpn.com/de/blog/wiper-malware/
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-malware/what-is-wiper-malware/
https://www.fortinet.com/blog/threat-research/the-increasing-wiper-malware-threat
https://www.microsoft.com/en-us/security/security-insider/microsoft-digital-defense-report-2023
https://www.microsoft.com/en-us/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/
Shamoon
https://attack.mitre.org/software/S0140/
https://www.securityweek.com/shamoon-3-attacks-targeted-several-sectors/
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/shamoon-attackers-employ-new-tool-kit-to-wipe-infected-systems/
https://securelist.com/shamoon-the-wiper-copycats-at-work/57854/
https://www.trendmicro.com/vinfo/de/security/news/cybercrime-and-digital-threats/new-version-of-disk-wiping-shamoon-disttrack-spotted-what-you-need-to-know
https://symantec.broadcom.com/hubfs/Attacks-Against-Critical_Infrastructrure.pdf
https://github.com/Neo23x0/signature-base/blob/master/yara/apt_shamoon2.yar
DarkSeoul
https://sansorg.egnyte.com/dl/nurZpNn8ee
https://www.usna.edu/CyberCenter/_files/documents/Operation-Blockbuster-Report.pdf
https://attack.mitre.org/groups/G0032/
https://malpedia.caad.fkie.fraunhofer.de/actor/lazarus_group
https://www.secureworks.com/research/wiper-malware-analysis-attacking-korean-financial-sector
https://github.com/kbandla/APTnotes/issues/260
NotPetya
https://attack.mitre.org/software/S0368/
https://www.secureworks.com/blog/notpetya-campaign-what-we-know-about-the-latest-global-ransomware-attack
https://www.cloudflare.com/learning/security/ransomware/petya-notpetya-ransomware/
https://www.cisa.gov/news-events/alerts/2017/07/01/petya-ransomware
https://analyze.intezer.com/files/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
https://www.virustotal.com/gui/file/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745/relations



