Wiper-Malware (Part 4)
In Part 3 of the malware wiper, it was observed that WhisperGate/WhisperKill and HermeticWiper, HermeticWizard and HermeticRansom were used before the Ukraine war and during the Ukraine conflict. Presumably to prepare for 24.02.2022. Directly on February 24, 2022, when Ukraine was invaded by the Russian military, three more wipers were detected on that day. These include AcidRain, with the Viasat attack, IsaacWiper and Neartwist.
AcidRain (alias Skyfall)
AcidRain is a wiper that can be linked to the Viasat satttack on February 24, 2022. A detailed analysis of AcidRain can be found in the post Voodoo Bear (APT44 - Part 2). In short, AcidRain deletes and overwrites files, rendering them unusable. It is not clear whether AcidRain was used again.
IsaacWiper and Neartwist
IsaacWiper and Neartwist are two wipers that are visible in the Mandiant and ESET timelines. Both were deployed between February 2022 and April 2022.
IsaacWiper (alias LASAINRAW)
IsaacWiper is a wiper written in C, C++ and Assembly. The wiper used on 24.02.2022 attacked Ukrainian government organizations, while the exact targets and the access vector are unknown. A timestamp of October 19, 2021, indicates that the attackers have been in the system since then. In addition, the remote access Trojan RemCom was also found on the infected system.
The wiper is a Windows DLL or EXE file (e.g. clean.exe, cl.exe, cl64.dll, cld.dll), which is saved under %programdata% or C:\Windows\System32.
First, the malware is started by an export function _Start@4. This export function is started with the command rundll32 <DLL_File>,#1 and is required because DLL files cannot be executed directly, but require a defined export function in order to be called by other processes (e.g. rundll32.exe). A log file is now saved under %ProgramData%\log.txt for debug information.
Log File- https://go.recordedfuture.com/hubfs/reports/mtp-2022-0324.pdf
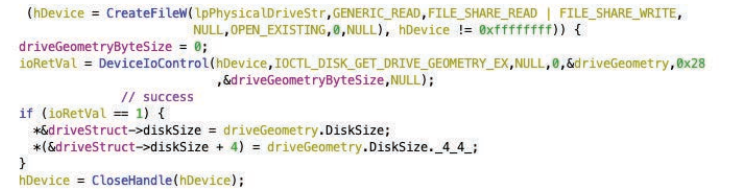
Now the drives and partitions are enumerated by creating handles to \PhysicalDrive<N> until an invalid handle is found. A handle is a unique identifier that an operating system (e.g. Windows) assigns to an object when a program accesses it. It acts as a pointer or reference to system resources such as files, processes, threads, registry keys or devices. The Windows system directory is then determined using the API function GetWindowsDirectoryW and the drive letter of the system directory is extracted and a handle for \.<DriveLetter>: is created.
Device information is also queried for each drive using the IOCTL calls via DeviceIoControl:
• IOCTL_STORAGE_DEVICE_NUMBER: Identifies the device and partition number
• IOCTL_DISK_GET_DRIVE_GEOMETRY_EX: Determines the size of the drive
To obtain a list of logical drives, GetLogicalDrives is also called. A handle with \.<DriveLetter>: is created for this purpose. To determine the associated physical hard disk, the query IOCTL_STORAGE_GET_DEVICE_NUMBER is also issued.
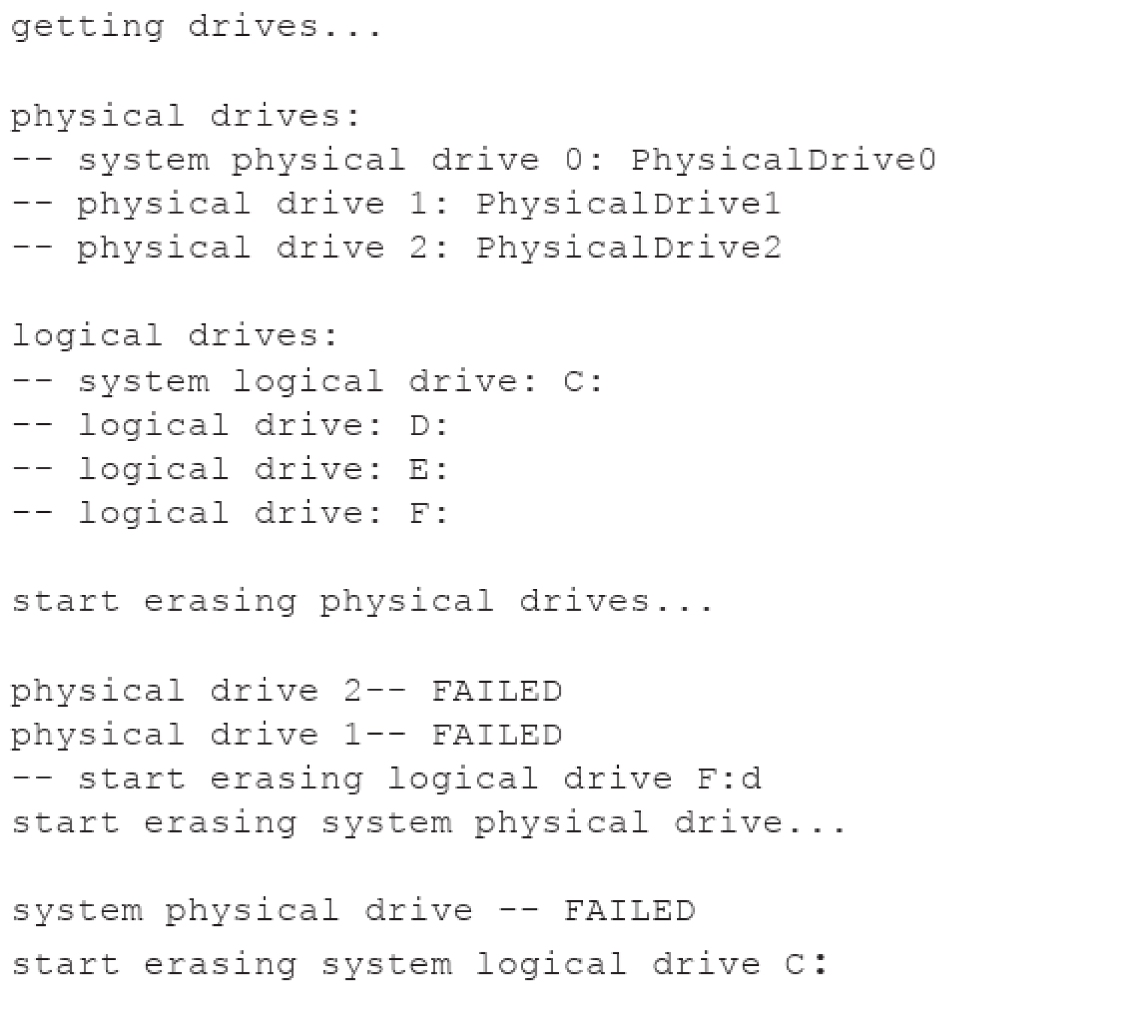
The wiping process is now started. For this, all physical drives except the OS drive are deleted in parallel in separate threads.
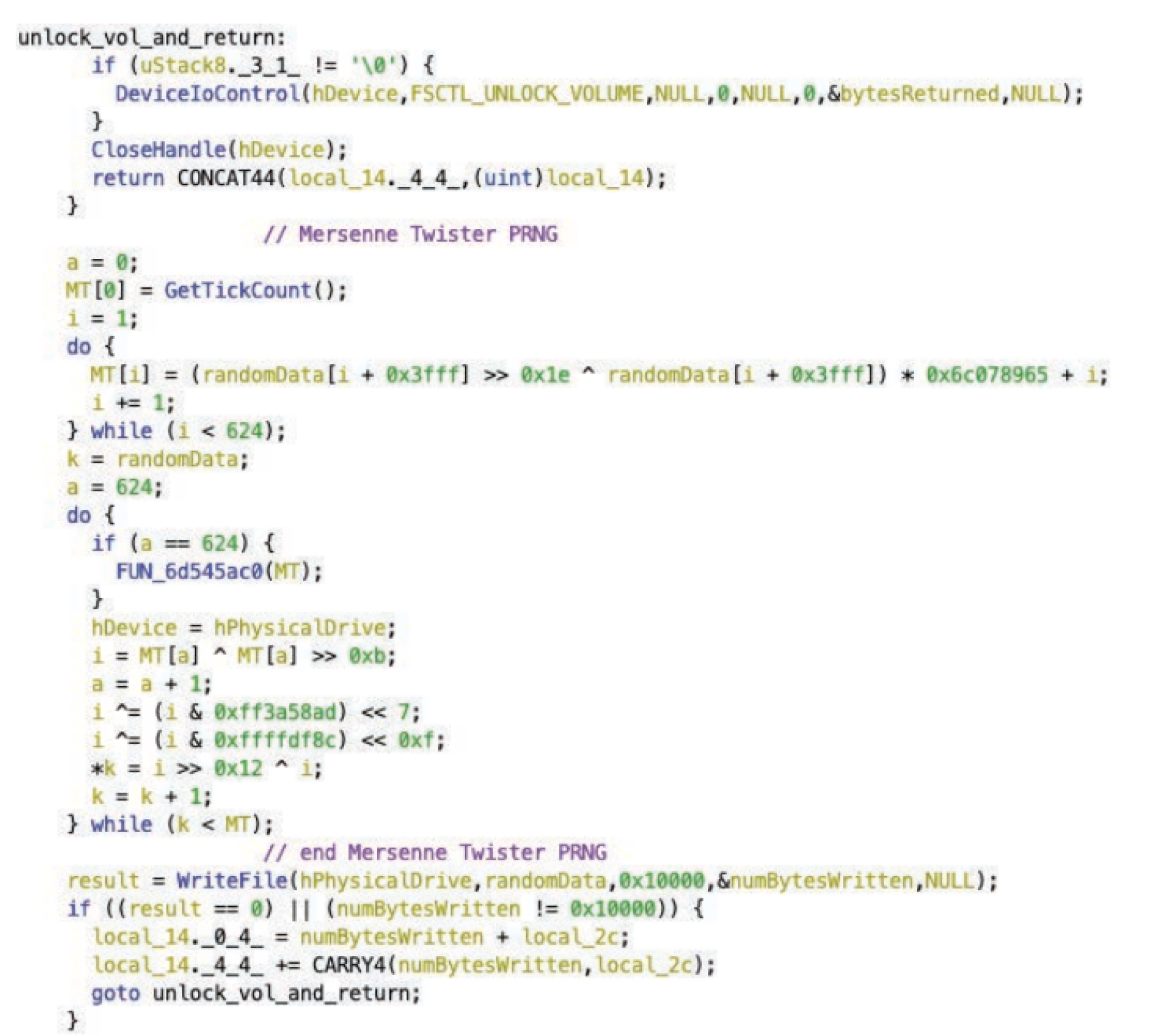
• FSCTL_LOCK_VOLUME: Locks the volume so that it cannot be used for other purposes
• Random data is generated using the Mersenne Twister PRNG algorithm and written in 64 KB blocks (0x10000 bytes)
The process runs until WriteFile fails
• FSCTL_UNLOCK_VOLUME is called to unlock the volume
Line of code for overwriting a physical drive with random data generated with the Mersenne Twister PRNG - https://go.recordedfuture.com/hubfs/reports/mtp-2022-0324.pdf
The logical drives are then deleted using the same method, with the OS drive is overwritten last. However, FSCTL_LOCK_VOLUME fails here when deleting the OS drive, which partially prevents write access. To ensure that the drive is no longer bootable, the first 64 KB of the Master Boot Record (MBR) are now overwritten 16 times with random values. This overwrites the data located in the first 512 KB of the drive.
Finally, a new thread is started to fill the entire free memory space of the OS drive with random data to make sure that all data has been overwritten, including data that has already been deleted, for example. For this purpose, a hidden directory Tmd<unique value>.tmp is created under C:\, in which temporary files Tmf<unique value>.tmp are filled with random data until the memory is full. At the same time, all files on the system drive are overwritten by writing random values to them in 64 KB blocks.
Now all data is overwritten and the system is no longer bootable.
Unfortunately, no exact information about tools could be found, but it is assumed that Impacket was used for lateral movements in addition to RemCom for remote access.
Another anomaly was that the attacker released a new version of IsaacWiper with debug logs on February 25, 2022. Various sources indicate that it is possible that not all target computers could be deleted.
Furthermore, some sources have suggested that there is a connection between HermeticWiper and IsaacWiper, which the short time span of the two attacks may suggest. According to Recorded Future, however, there is no code overlap with HermeticWiper or WhisperGate. Based on this and other indicators, there is also no assumption as to which actor is responsible for this attack, due to the timing, the current situation and the fact that no money is being extorted and therefore there is no financial motivation behind it, could point to a Russian state-sponsored actor.
It is not clear whether IsaacWiper was used again.
SentinelLab has published Yara-Rules for this purpose. - https://github.com/SentineLabs/Yara/blob/main/APT_RU_SunFlowerSeed.yar
Neartwist
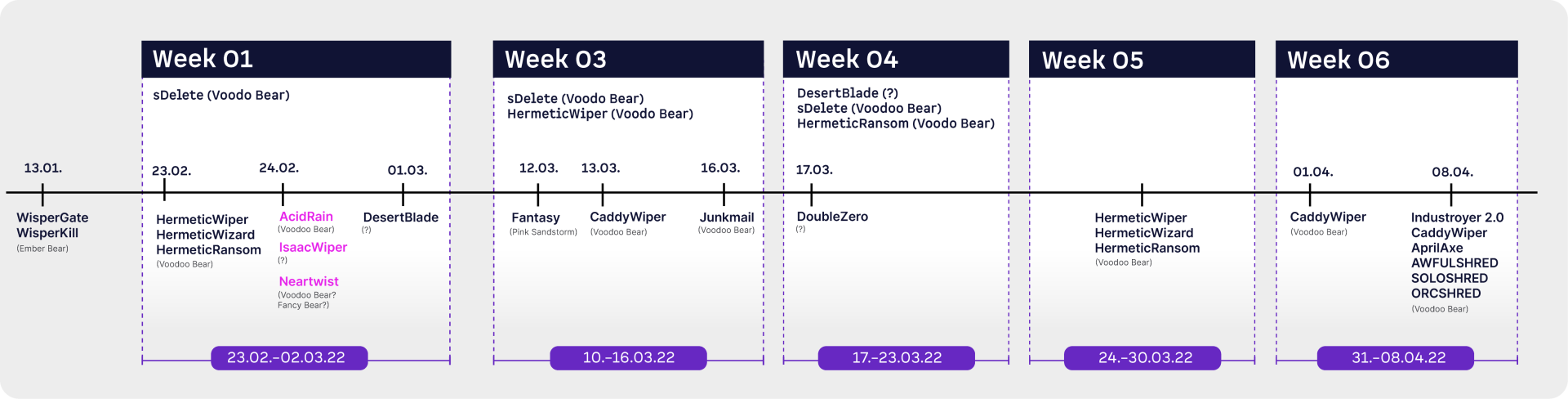
Neartwist is a wiper for which very little information can be found. Mandiant has made two assumptions as to which actor could be behind Neartwist. One is Fancy Bear (aka APT28 - post dated 29.06.2022) and Voodoo Bear (APT44 - post dated 17.04.2024), which are both of which are Russian state-sponsored actors. A Mandiant post by In general, it can be said that the wiper was programmed in C and, according to Mandiant, lists the physical drives and tries to delete or overwrite them, which were randomly generated. In general, Neartwist could only be identified by Mandiant and could only be found in the Mandiant timeline and no other posts (see images).
The absence of WhisperKill and IsaacWiper in the Mandiant graphics, as well as the absence of Neartwist in the ESET graphics, suggest that this could be an alias of one of these two wipers. Looking at the graphics further, it is noticeable that the Microsoft timeline does not begin until February 2022. In addition, it is assumed that the player behind WhisperGate is Ember Bear. Both points, as well as the position of Neartwist, indicate that this is IsaacWiper. Despite initial assumptions, there is no known connection to HermeticWiper.
left: Mandiant Timeline - https://blog.google/threat-analysis-group/fog-of-war-how-the-ukraine-conflict-transformed-the-cyber-threat-landscape/
right: ESET Timeline - https://www.welivesecurity.com/2023/02/24/year-wiper-attacks-ukraine/
For further research
IsaacWiper
• https://www.welivesecurity.com/2022/03/01/isaacwiper-hermeticwizard-wiper-worm-targeting-ukraine/
DE: https://www.welivesecurity.com/deutsch/2022/03/01/isaacwiper-und-hermeticwizard-neue-cyber-angriffe-in-der-ukraine/
• https://www.eset.com/int/about/newsroom/press-releases/research/eset-research-ukraine-hit-by-destructive-attacks-before-and-during-the-russian-invasion-with-hermet/
DE: https://www.eset.com/de/about/presse/pressemitteilungen/pressemitteilungen/ukraine-von-weiteren-gezielten-cyberattacken-betroffen/
• https://www.cisa.gov/news-events/analysis-reports/ar22-115
• https://www.ncsc.gov.uk/news/organisations-urged-to-bolster-defences
• https://go.recordedfuture.com/hubfs/reports/mtp-2022-0324.pdf
• https://msrc.microsoft.com/blog/2022/02/analysis-resources-cyber-threat-activity-ukraine/
• https://malpedia.caad.fkie.fraunhofer.de/details/win.isaacwiper
• https://www.welivesecurity.com/deutsch/2022/11/29/ransomboggs-neue-ransomware-attackiert-die-ukraine/
• https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
• https://www.threatdown.com/blog/double-header-isaacwiper-and-caddywiper/
• https://www.recordedfuture.com/blog/isaacwiper-continues-trend-wiper-attacks-against-ukraine
• https://securityintelligence.com/posts/new-wiper-malware-used-against-ukranian-organizations/
• https://www.bpb.de/system/files/dokument_pdf/UkraineAnalysen267.pdf?download=1
Neartwist
• www.nts.eu/app/uploads/2024/10/20240910_Cyber-Domaine-im-Militaer-scharwitzl-ExecutiveDaysAustria24-WEST.pdf
• https://cloud.google.com/blog/topics/threat-intelligence/burrowing-your-way-into-vpns/?hl=e
• https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
• https://services.google.com/fh/files/blogs/google_fog_of_war_research_report.pdf
• https://cloud.google.com/blog/topics/threat-intelligence/apt44-unearthing-sandworm?hl=en