Wiper-Malware (Part 3)
This blog post follows on from Part 1 and Part 2 of my wiper analysis and focuses specifically on the attacks that took place on January 13 and February 23, 2022. In particular, I will focus on WhisperGate and WhisperKill, HermeticWiper, HermeticWizard and HermeticRansom.
In the last few years, wiper attacks have become a weapon of choice in geopolitical conflicts - especially in the context of the Russia-Ukraine war. While well-known wipers such as Shamoon, NotPetya or GermanWiper have already caused great damage in previous attacks, a new wave of destructive malware was observed in 2022.
I will not only go into the technical details of the various wipers, but also shed light on the attack patterns and possible actors behind the attacks. A detailed timeline will also provide an overview of how the wiper attacks developed over the course of the first months of the war from January and February to April.
WhisperGate (alias PAYWIPE) and WhisperKill (alias Shadylook)
The WhisperGate wiper is believed to have been used by the Russian state-sponsored threat actor Ember Bear (aka DEV-0586) and co-sponsored to destroy corporate networks in January 2022 by overwriting and deleting files.
In the attack, the group compromised systems of the Ukrainian government and IT sector on January 13, 2022. It is believed that the attackers were able to gain access to the companies through supply chain attacks, OctoberCMS, whereby it is a self-hosted content management system, and Log4j.
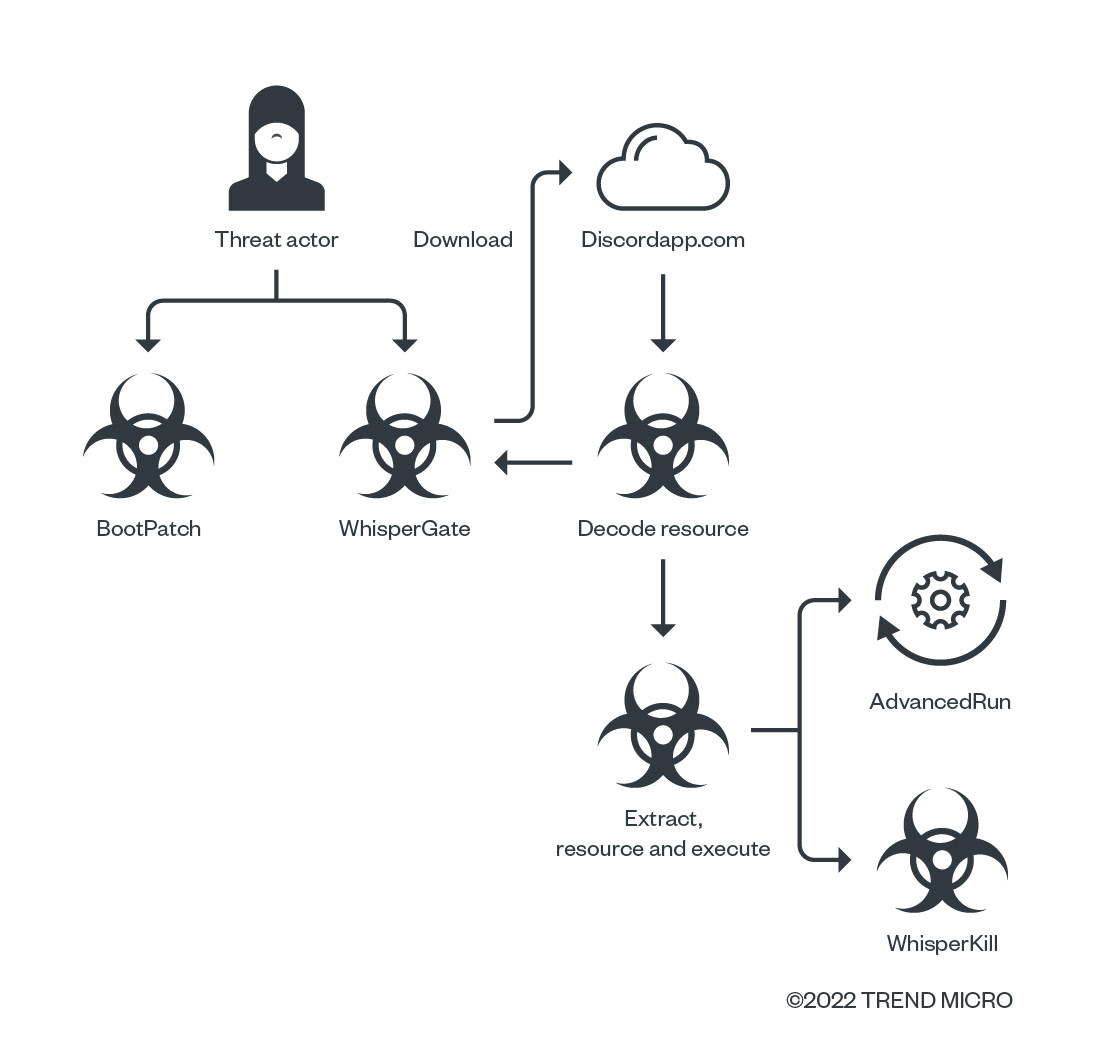
First, the actor distributes two malware components. One is Bootpatchand the other is WhisperGate.
Bootpatch or stage1[.]exe is a wiper that overwrites the master boot record (MBR) of the infected system, making it impossible to start the respective system. In addition, a fake ransom note is displayed to give the impression of a ransomware attack.

WhisperGate - Fake Message - https://www.crowdstrike.com/en-us/blog/technical-analysis-of-whispergate-malware/?utm_source=chatgpt.com
WhisperGate is used as a dropper, which in this case downloads additional, encrypted malicious code from an external source. In this case, Discordapp[.]com is misused as the C&C (Command and Control) server, as these are usually less frequently blocked by firewalls.
Next, the encrypted malicious code is decrypted by a decode resource. This malicious code component contains WhisperKill, which is used in the Extract, resource and execute step (refer to WhisperGate Attack Chain picture). This step also ensures that the malicious file is running with the correct priviligations.
AdvancedRun is executed at the Extract, resource and execute step. AdvancedRun is a legitimate tool from NirSoft that allows programs to be executed with administrator rights. These administrator rights are required so that WhisperKill contains all the necessary rights for further malicious activity. In addition, this program helps to bypass security measures such as User Account Control (UAC).
Finally, WhisperKill or stage2[.]exe is executed, which lists all drives A to Z. Just like Bootpatch, this is also a wiper, but WhisperKIll aims to overwrite files on connected drives that are of type 3 (DRIVER_FIXED - Removable medium (e.g. USB stick, SD card, floppy disk drive)) or 4 (DRIVER_REMOTE - Hard disk or SSD (permanently installed drive)) with certain extensions and delete them irrevocably.
WhisperKill - List of endings - https://www.trendmicro.com/de_de/research/22/c/cyberattacks-are-prominent-in-the-russia-ukraine-conflict.html
In summary, the system can no longer boot due to the overwritten Master Boot Record (MBR) and all files with predefined endings, which were also overwritten and then irrevocably deleted, are lost.
https://github.com/Neo23x0/signature-base/blob/master/yara/apt_ua_wiper_whispergate.yar
HermeticWiper (alias Foxblade, Nearmiss, DriveSlayer, KillDisk.NCV), HermeticWizard and HermeticRansom (alias SonicVote)
HermeticWiper is a malware that can be linked to the attack on Ukrainian organizations on 23.02.2022, among others. According to CISA, this attack was discovered by cyber security researchers on February 23, 2022 and, according to Mandiant, can be linked to the Russian state-sponsored threat actor Voodoo Bear (aka Sandworm, APT44). SentinelLab points out, the technique used here is similar to that used by Lazarus Group and APT33.
Mandiant APT44 Distuptive Tools - https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
In the case of HermeticWiper, the time of compromise is very difficult to determine, but a timestamp of the malware dated 28.11.2021 indicates that the affected organizations could have been compromised as early as the end of 2021. According to Symantec, it is possible that the attackers gained access to the organizations' network on 23.12.2021 via malicious SMB activity against a Microsoft Exchange Server (CVE-2021-1636).
Login credentials were then stolen. On January 16, 2021, a web shell was installed.
Now the actors executed a PowerShell command, which was made possible by a Tomcat vulnerability. This PowerShell command was used to download a JPEG file from a victim's internal network.
Presumably these JPEG file contain malicious code or similar. Next, the actors create a scheduled task. Here, the file “postgresql[.]exe” was executed weekly on Wednesday at 11:05 local time.
A few minutes later, the time was changed to 09:30 local time.
Symantec observed that the file “postgresql[.]exe” was used to run certutil to verify connectivity to trustsecpro[.]com and whatismyip[.]com. Certutil is a command line tool integrated into Windows that is used to manage certificates and certification authorities. It is part of the Windows Certificate Services and enables various operations such as displaying, installing and exporting certificates. In addition, this file executes a PowerShell command which downloads another JPEG file from the web server confluence[.]novus[.]ua. Presumably these JPEG files contain malicious code or similar.
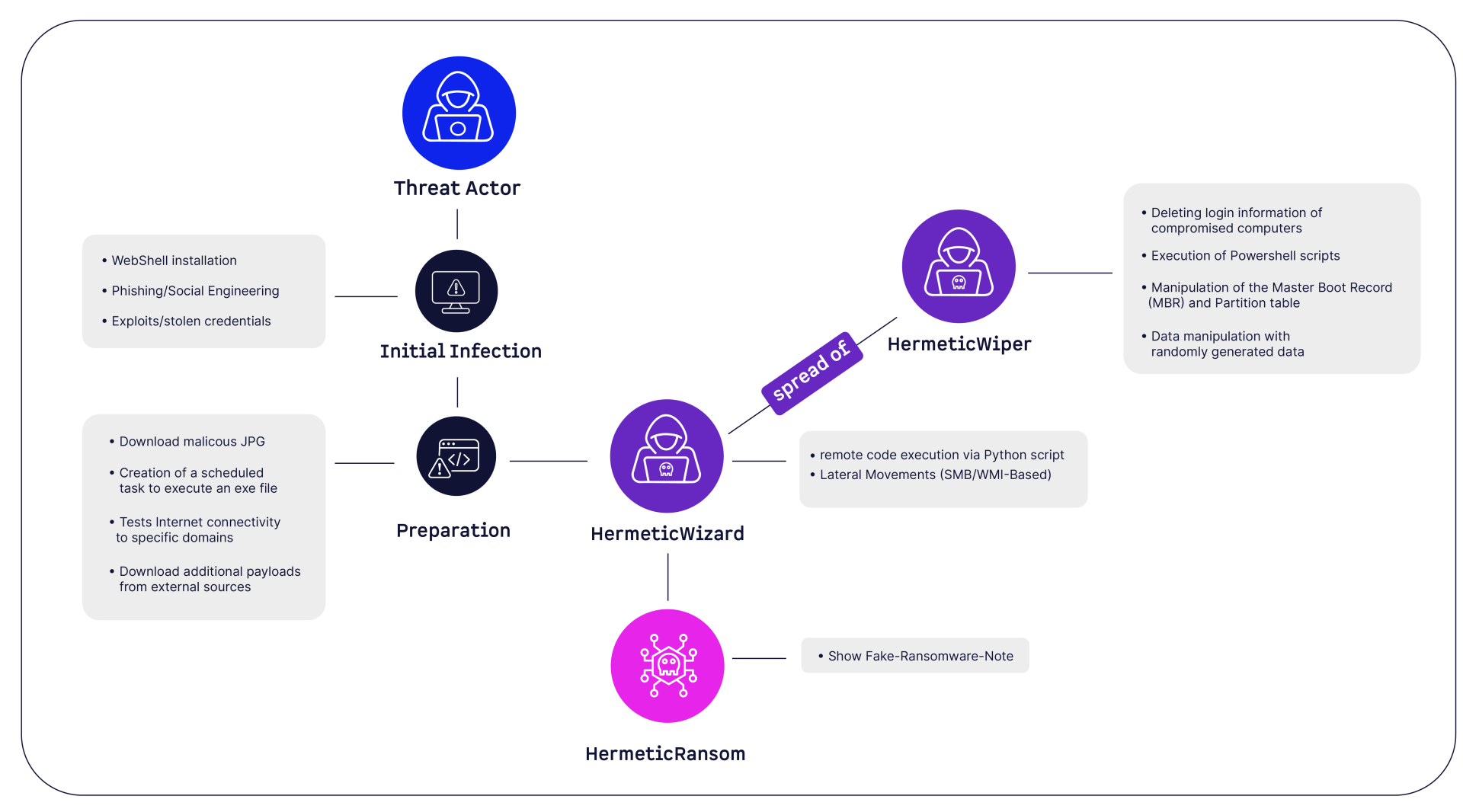
After preparations were completed, the HermeticWizard worm was deployed with the command regsvr32[.]exe /s /i <path> on February 23, 2022. According to Microsoft, regsvr32[.]exe is “a command-line utility to register and unregister Object Linking and Embedding (OLE) controls, such as DLLs and ActiveX controls in the Windows Registry” (Microsoft, as of March 7, 2025, “How to use the Regsvr32 tool and troubleshoot Regsvr32 error messages”). This was done to identify computers on the network and infect them via the Windows functions:
• DNSGetCacheDataTable - Retrieves the cached DNS entries (DNS cache) of the system
• GetIpNetTable - Returns the ARP table of the system. This table contains mappings between IP addresses and MAC addresses
• WNetOpenEnumW(RESOURCE_GLOBALNET, RESOURCETYPE_ANY) - Enables the listing of network resources (e.g. shared folders, network printers).
• NetServerEnum - Lists all computers in a Windows domain or workgroup
• GetTcpTable - Retrieves a table with all open TCP connections and their status
• GetAdaptersAddresses - Retrieves information about all network interfaces (adapters) of the system, including IP addresses, MAC addresses and connection types.
In addition, wmiexec[.]py is used to execute remote code, which is used with Impacket, a script-based open source solution, for remote code execution. Finally, HermeticWizard distributes the HermeticWiper.
The spread of HermeticWiper is now deleting credentials from infected devices and running three PowerShell scripts, the effects of which are unknown.
• powershell -v 2 -exec bypass -File text.ps1
• powershell -exec bypass gp.ps1
• powershell -exec bypass -File link.ps1
The malware also focuses on corrupting the following locations:
• Master Boot Record (MBR)
• Master File Table (MFT)
• $Bitmap and $LogFile on all drives
• The files with the registry keys (NTUSER*)
• C:\Windows\System32\winevt\Logs
Among other things, HermeticWiper enumerates all partitions for all possible drives and distinguishes between FAT and NTFS partitions. For a FAT partition, the Windows API function CryptGenRandom is called, which creates random bytes and overwrites the data with them. For NTFS partitions, the wiper first analyzes the master file table and only then executes the Windows API function CryptGenRandom.
In addition, folders and (subordinate) files in the Windows, Programme, Programme (x86), PerfLogs, Boot, System Volume Information and AppData folders are recursively deleted by an FSCTL_MOVE_FILEoperation. Large files and symbolic links in “My Documents” and “Desktop” are also overwritten. The computer is then restarted to complete the process and ensure that the data cannot be restored. Restarting is no longer possible due to the deletion of the MBR file.
It was noticeable that four different embedded drivers could be found in HeremticWiper, which, depending on the Windows operating system version, one of these drivers is selected and stored under C:\Windows\System32\drivers\<4 zufällige Buchstaben>.sys.
• 0E84AFF18D42FC691CB1104018F44403C325AD21: x64-driver
• 379FF9236F0F72963920232F4A0782911A6BD7F7: x86-driver
• 87BD9404A68035F8D70804A5159A37D1EB0A3568: x64 XP-driver
• B33DD3EE12F9E6C150C964EA21147BF6B7F7AFA9: x86 XP-driver
Parallel to the HermeticWiper process, the HermeticRansom displays a fake ransomware note, giving the appearance of a “normal” ransomware attack.

HermeticRansom - Fake Message - https://www.kaspersky.de/blog/hermeticransom-hermeticwiper-attacks-2022/28234/
The malware also analyzes all hard disks and files that are stored outside the “Windows” and “Programs” folders. HermeticRansom now encrypts the analyzed data with the extensions .inf, .acl, .avi, .bat, .bmp, .cab, .cfg, .chm, .cmd, .com, .crt, .css, .dat, .dip, .dll, .doc, .dot, .exe, .gif, .htm, .ico, .iso, .jpg, .mp3, .msi and odt. These are now also marked as “encrypted” and provided with the email address of the ransomware operators.

HermeticRansom - DataName - https://go.recordedfuture.com/hubfs/reports/mtp-2022-0302.pdf
Once the attack is complete, HermeticWiper deletes itself from the hard disk by overwriting itself with randomly generated bytes, which is presumably intended to make analysis more difficult.
In the APT Activity Report T3 2022, ESET refers to a new version of HermeticWiper, which was uploaded to VirusTotal on October 5, 2022, but no exact details of attacks are available.
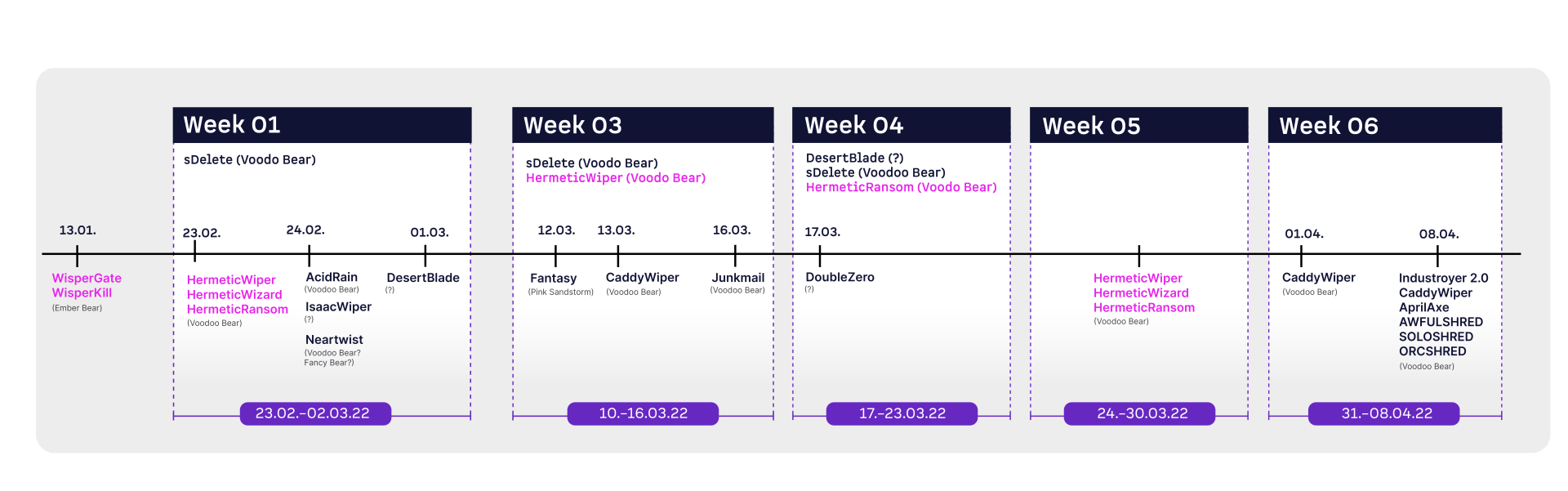
In the report “An overview of Russia's cyberattack activity in Ukraine”, Microsoft also refers to activities by HermeticWiper (alias FoxBlade) in Week 3 (March 10-16) and Week 5 (March 24-30). Exact information on this is also not available.
The same Microsoft report also referred to activity by HermeticRansom (aka SonicVote) in Week 4 (March 17-23) and Week 5 (March 24-30).
As of March 03, 2022, the ransomware was detected on January 16, 2025 at 12:02:56 UTC HermeticWiper
Florian Roth has published Yara-Rules for this purpose. - https://github.com/SentineLabs/Yara/blob/main/APT_RU_SunFlowerSeed.yar
Conclusion
The WhisperGate and WhisperKill attacks on January 13, 2022, and HermeticWiper, HermeticWizard and HermeticRansom on February 23, 2022, show how destructive malware is used in hybrid conflicts. While WhisperGate and WhisperKill marked the first major cyberattack in the context of the Russia-Ukraine war, the HermeticWiper attack underlines the escalating threat situation shortly before the invasion.
Both campaigns make it clear that the attackers were not interested in financial extortion - as is the case with classic ransomware - but in the irreversible destruction of data and systems. The wipers used were introduced into the networks with great precision and showed once again how effectively modern attacks can spread via supply chain gaps, stolen login data and legitimate system tools.
For further research
WhisperGate and WhisperKill
• https://x.com/esetresearch/status/1483161464106098689
• https://x.com/hashtag/WhisperGate?src=hashtag_click
• https://www.microsoft.com/en-us/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/
• https://x.com/MsftSecIntel/status/1482543129454686215
• https://malpedia.caad.fkie.fraunhofer.de/details/win.whispergate
• https://attack.mitre.org/software/S0689/
• https://msrc.microsoft.com/blog/2022/02/analysis-resources-cyber-threat-activity-ukraine/
• https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
• https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-057a
• https://unit42.paloaltonetworks.com/ukraine-cyber-conflict-cve-2021-32648-whispergate/#whispergate-malware-family
• https://www.cybereason.com/blog/research/cybereason-vs.-whispergate-wiper
• https://www.trendmicro.com/de_de/research/22/c/cyberattacks-are-prominent-in-the-russia-ukraine-conflict.html
• https://www.fortinet.com/blog/threat-research/the-increasing-wiper-malware-threat
• https://therecord.media/a-deeper-look-at-the-malware-being-used-on-ukrainian-targets?utm_source=chatgpt.com
• https://cert.gov.ua/article/18101
• https://logging.apache.org/log4j/2.x/index.html
HermeticWiper, HermeticWizard and HermeticRansom
• https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-057a
• https://unit42.paloaltonetworks.com/preparing-for-cyber-impact-russia-ukraine-crisis/
• https://www.cisa.gov/news-events/analysis-reports/ar22-115a
• https://therecord.media/second-data-wiper-attack-hits-ukraine-computer-networks
• https://www.eset.com/int/about/newsroom/press-releases/research/eset-research-ukraine-hit-by-destructive-attacks-before-and-during-the-russian-invasion-with-hermet/
• DE: https://www.eset.com/de/about/presse/pressemitteilungen/pressemitteilungen/ukraine-von-weiteren-gezielten-cyberattacken-betroffen/
• https://www.welivesecurity.com/2022/03/01/isaacwiper-hermeticwizard-wiper-worm-targeting-ukraine/
• DE: https://www.welivesecurity.com/deutsch/2022/03/01/isaacwiper-und-hermeticwizard-neue-cyber-angriffe-in-der-ukraine/
• https://msrc.microsoft.com/blog/2022/02/analysis-resources-cyber-threat-activity-ukraine/
• https://www.welivesecurity.com/deutsch/2022/11/29/ransomboggs-neue-ransomware-attackiert-die-ukraine/
• https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
• https://www.virustotal.com/gui/file/1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591/detection
• https://x.com/threatintel/status/1496578746014437376
• https://x.com/juanandres_gs/status/1496581710368358400
• https://thehackernews.com/2022/02/new-wiper-malware-targeting-ukraine.html
• https://www.sentinelone.com/labs/hermetic-wiper-ukraine-under-attack/
• https://www.security.com/threat-intelligence/ukraine-wiper-malware-russia
• https://www.kaspersky.de/blog/hermeticransom-hermeticwiper-attacks-2022/28234/
• https://go.recordedfuture.com/hubfs/reports/mtp-2022-0302.pdf
• https://www.virustotal.com/gui/file/1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591/details
• https://support.microsoft.com/en-us/topic/how-to-use-the-regsvr32-tool-and-troubleshoot-regsvr32-error-messages-a98d960a-7392-e6fe-d90a-3f4e0cb543e5