Voodoo Bear (APT44 - Part 1)
Alias: ELECTRUM, Telebots, IRON VIKING, BlackEnergy (Group), Quedagh, Voodoo Bear, IRIDIUM, Seashell Blizzard, FROZENBARENTS
In modern cyber warfare, not only independent hacker groups utilize digital arsenals, but states also deploy these means to enforce their interests. One prominent example is the Russian hacker group APT44, also known as "Voodoo Bear," which operates on behalf of the Russian state. This group has been linked to several significant cyberattacks, including the attack on Viasat in 2022, the 2018 Olympic Games, and the NotPetya malware in 2017. These attacks demonstrate that the scope of cyber warfare extends beyond military conflict, impacting regular organizations, businesses, and even large international events.
Given the far-reaching consequences of such attacks, it is crucial to understand how to defend against them. Analyzing the malware used by these groups and developing effective threat-hunting queries are essential steps in building resilience. Proactive defense strategies help mitigate risks not only in conflict zones but also in everyday organizational contexts.
Voodoo Bear (Sandworm)
Voodoo Bear, which is primarily known as Sandworm and, as can be seen in the hierarchical diagram, presumably reports to the General Staff Main Intelligence Directorate (GRU), just like Fancy Bear aka APT28. These were also classified as an Advanced Persistent Threat (APT44) in April 2024.
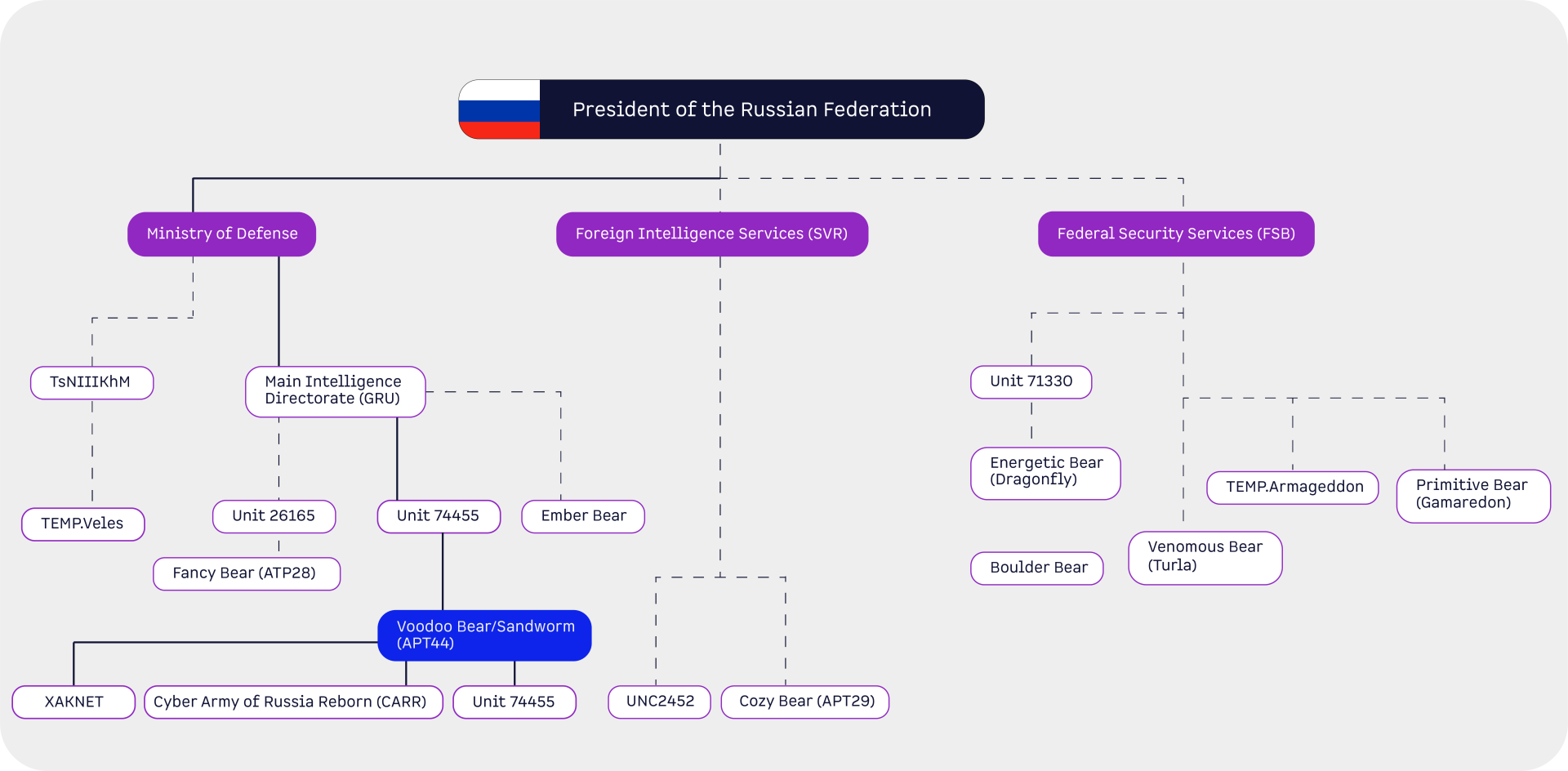
Voodoo Bear, which is also known as IRIDIUM, should not be confused with the Iranian hacker group of the same name, IRIDIUM.
The group is particularly interested in Ukraine, NATO, Georgia, South Korea, the Middle East and Central Asia. The sectors are in line with Fancy Bear:

https://services.google.com/fh/files/blogs/google_fog_of_war_research_report.pdf
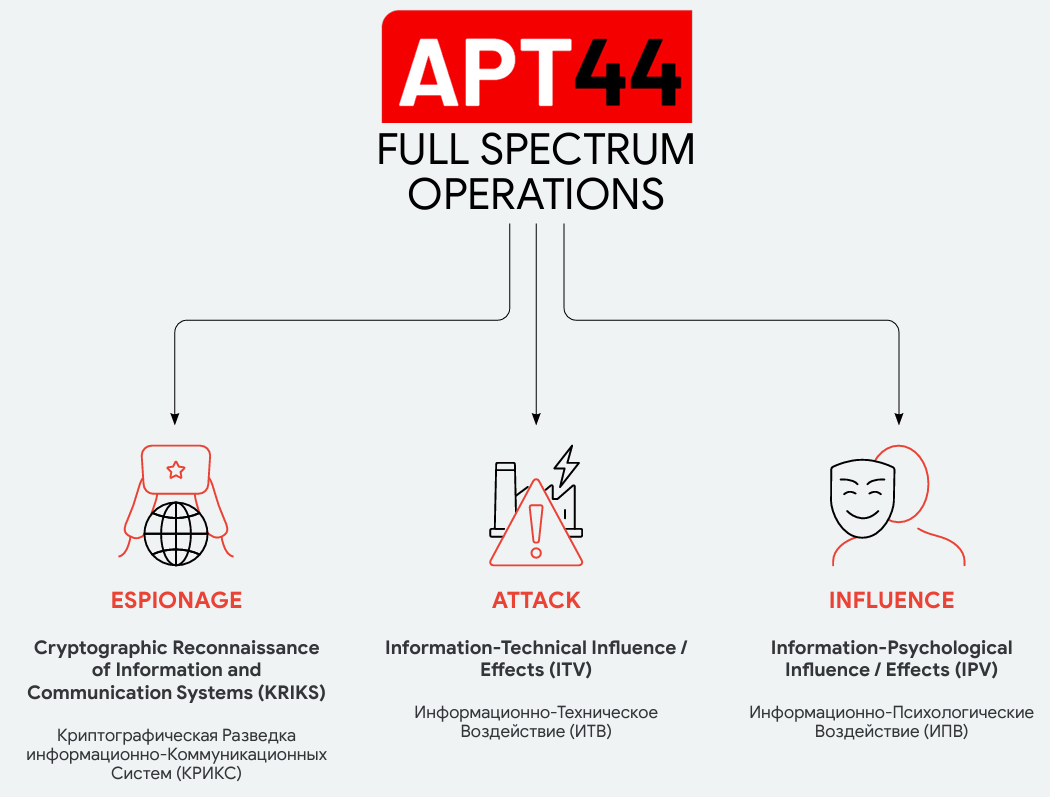
APT44 motivation mainly relates to three points, which show strong overlaps with the motivations of APT28 and APT29. The first motivation is espionage, e.g. to find out the different interests of opponents.
The second motivation is influence, i.e. information psychological influence/impact (IPI), which was used, for example, in the APT28 attack on the 2016 US elections, in which information was obtained and leaked at the right time in order to influence society to achieve the desired success. The last motivation is the attack, i.e. the information technology influence/effect (ITV).
https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
According to Mandiant, the hacker group primarily focuses on hack-and-leak and attack-and-leak operations that are posted on a Telegram channel to generate attention for their work. In addition, hacktivist Telegram channels such as XAKNET, Cyber Army of Russia Reborn (CARR) and Solntsepek (see hierarchical diagram) are associated with Voodoo Bear.
Attack
Hacker attacks are no longer exceptional news, as they happen every day all over the field. In January 2024, Voodoo Bear also gained access to a water utility company in Texas. The video shows a screen recording of the attack, in which the attacker changes settings etc.
“A screen recording shows Cyber Army of Russian Reborn clicking buttons on the interface of a water utility in Texas“ - https://www.wired.com/story/cyber-army-of-russia-reborn-sandworm-us-cyberattacks/
In addition to the attack at the beginning of the year, there have been more and more attacks with a strong impact in recent years. One such attack is, for example, the hack-and-leak campaigns in the 2016 US elections, which presumably involved not only Fancy Bear or APT28, but also Voodoo Bear according to Mandiant's records. Other attacks included the elections in France, the Olympic Games and a serious attack on Viasat, which led to an internet outage for around 30,000 customers, including the Ukrainian military.
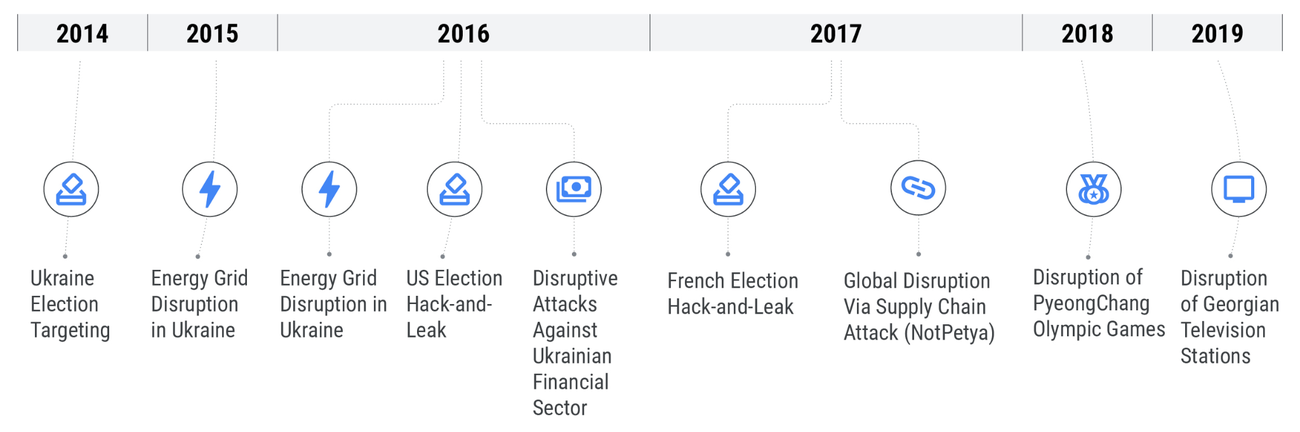
Timeline of pre-war operations - https://cloud.google.com/blog/topics/threat-intelligence/apt44-unearthing-sandworm?hl=en
Viasat
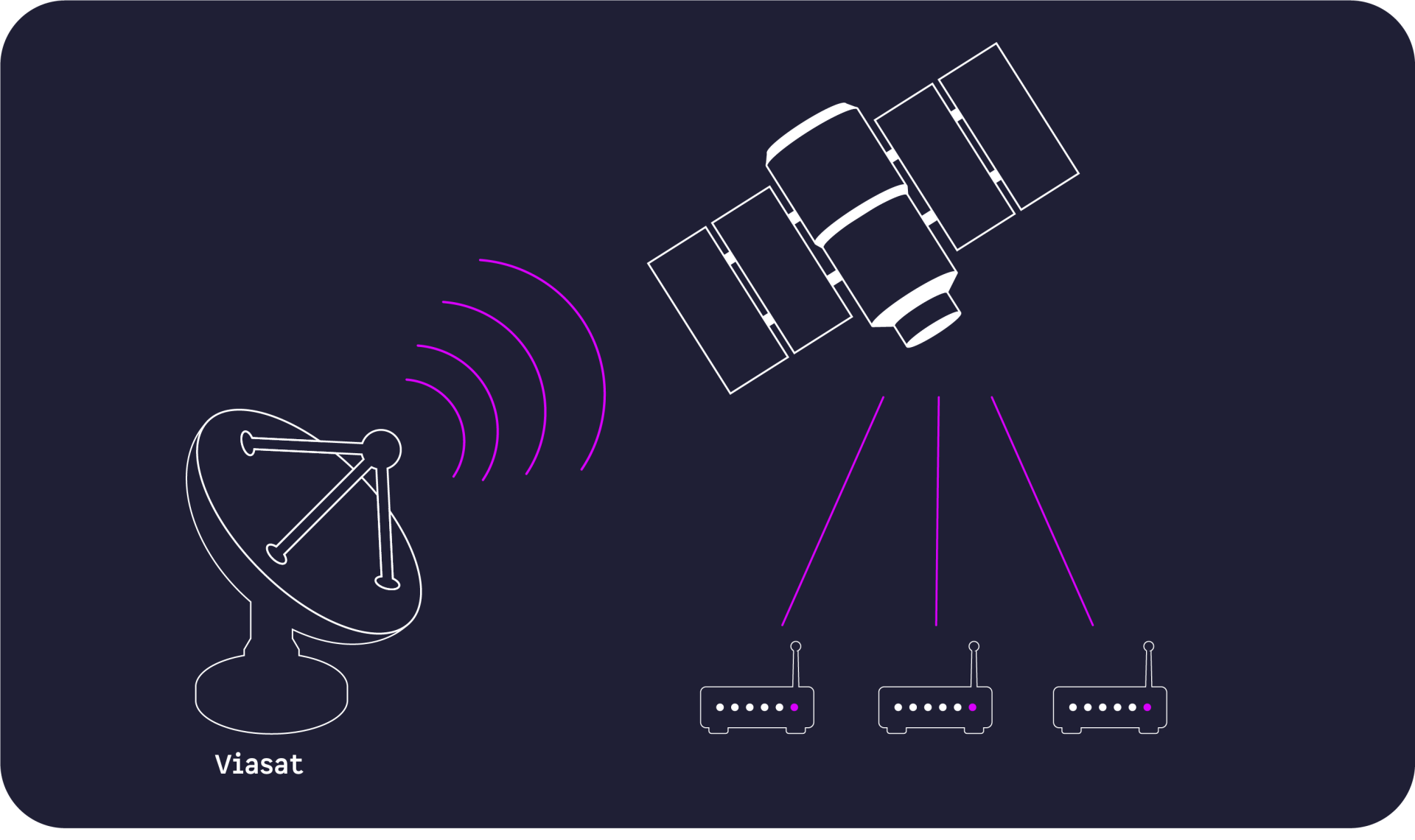
On February 24, 2022 at 03:02 UTC, the first activities of an attack by Viasat employees were detected. Viasat is a communications company that offers satellite internet. Notable was a high volume of malicious and targeted traffic directed at the SurfBeam and Surfbeam2+ modems, as well as “associated customer premises equipment (CPE)”, most of which were located in Ukraine “and served by one of KA-SAT's consumer-facing network partitions” (Viasat, 2022, “KA-SAT Network cyber attack overview”).
This denial of service (DoS) attack caused many modems to go offline due to the load. The remaining modems that resisted the attack were taken offline by Viasat and Skylogic staff, but this led to the emergence of more malicious modems. To summarize, the service was originally provided by Euralsat but is now managed by Skylogic due to a transition plan.
At around the same time, according to Viasat, a decline in the number of modems connected online in Ukraine is visible. Presumably this is an additional decline than the modems that have already gone offline. At 04:15 UTC, further modems in Europe lost the network within 45 minutes, as they lost their connection to the network and no attempt was made to reconnect.
From this point onwards, no remote monitoring or control could be carried out on around 5,800 wind turbines in Germany due to the attack. Despite the lack of monitoring and control, the wind turbines ran the whole time.
The modems that went offline in Europe are due to the fact that the flash memory was overwritten during an attack, as a result of which the modem no longer had access to the network. Despite the overwriting of the flash memory, the modems are not unusable according to Viasat, as they can be restored with a factory reset. In addition to “over-the-air updates”, which are carried out via wireless interfaces such as WLAN or via the mobile network, around 30,000 modems were already sent to those affected at the end of March in order to ensure rapid availability.
In its incident report, Viasat states that no customer data or customer equipment such as PCs is affected.
SentinelLab's assumption, which was confirmed by Viasat, is that the attackers gained access to the trust management segment of the KA-SAT network through a misconfigured VPN appliance and used the KA-SAT management mechanism in a supply-chain attack to infiltrate the Wiper Acid Rain.

Day 1 - https://www.bbc.com/pidgin/world-60598588
During the 45 minutes in which the European modems were attacked, the Russian military invaded Ukraine. It is believed that since the Ukrainian military is a customer of Viasat, the Viasat hack was intended to disrupt or paralyze the Ukrainian military's communications. According to Victor Zhora, the former Chief Digital Transformation Officer of the SSSCIP (State Service of Special Communications and Information Protection of Ukraine) (2021 - 2023), the military only uses communication via the satellite network as a backup communication channel.

Victor Zhora - https://therecord.media/second-cyber-official-detained-zhora
It is important to mention that Victor Zhora was arrested in 2023 for embezzlement. According to his LinkedIn profile, Victor Zhora has been employed by ICE Task Force as a Board Member since February 2024.
Ukraine Electric Power Attack
There were already attacks on the Ukrainian energy supply during the Ukraine conflict, which began on February 20, 2014.
In the first attack on December 23, 2015, which affected the three Ukrainian energy suppliers Prykarpattyaoblenergo, Kyivoblenergo and Chernivtsioblenergo and thus the regions of Ivano-Frankivsk in western Ukraine, Kiev and Chernivtsi, the system was infiltrated due to spear phishing emails with malicious attachments from Sandworm. The malicious attachment installed the BlackEnergy 3 malware, which gave Sandworm access to the system and gained administrator access to SCADA (Supervisory Control and Data Acquisition) systems.
Since these SCADA systems are used to control the power grid, the attackers were able to activate a switch and thus cause a power outage. The activation of this switch resulted in 230,000 people being without power for between one and six hours. To hinder the restoration of the power grid, Sandworm installed KillDisk malware to render SCADA unusable. KillDisk overwrote the firmware of devices.
In addition, the utility's telephone exchange was paralyzed by DDoS attacks. It is suspected that the aim of the Russian state-sponsored actors was to destabilize Ukraine, demonstrate power and undermine the trust of the people living in Ukraine in individual institutions
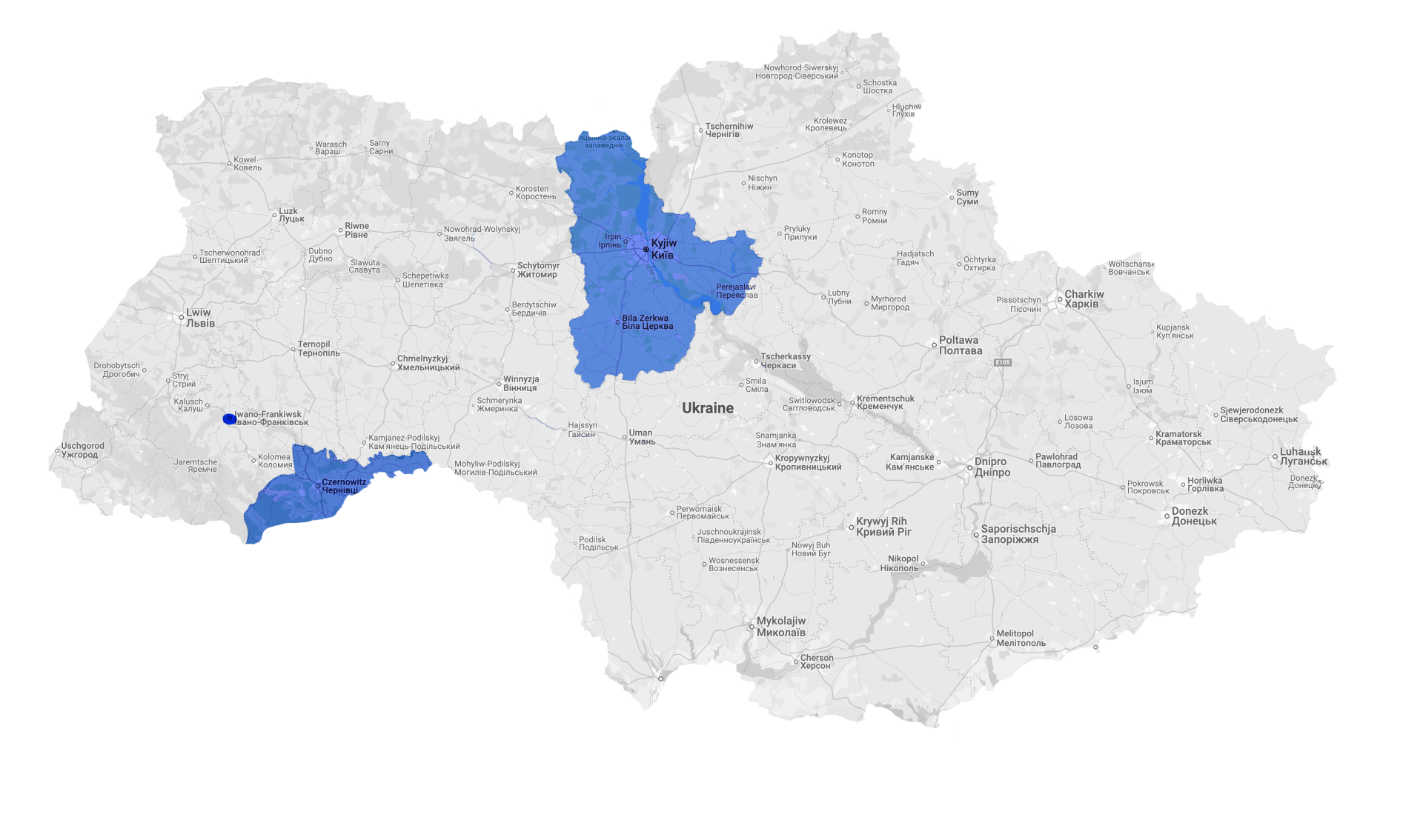
The attack on the Ukrainian power supply on December 17, 2016, at around midnight, mainly targeted parts of Kiev and its surroundings and therefore only affected 200,000 people, 30,000 fewer than the attack a year earlier.
It is assumed that the attackers had already penetrated the energy supplier's system months earlier through a security gap in ICS components and phishing, for example.
The attackers installed the malware Industroyer, which communicates with the industrial control systems (e.g. via IEC 104 protocol) and was able to switch switches in substations on and off in a targeted manner, which led to an interruption in the power supply of around one hour. After the attackers switched off the power supply, the attackers blocked the restoration of this with additional attacks.
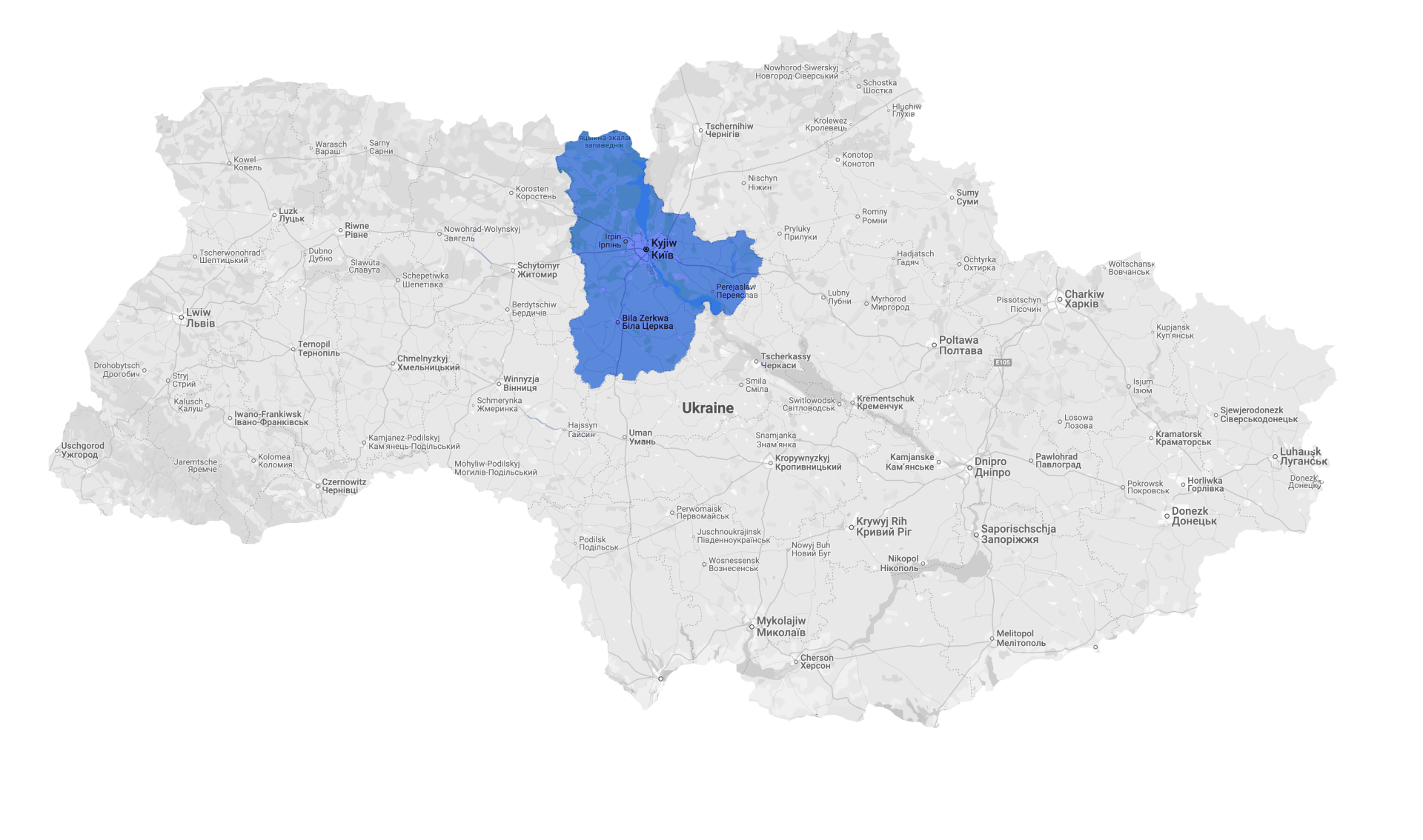
In the last known cyberattack on the Ukrainian power supply on April 8, 2022, Industroyer2, another development of the malware that was already used in 2016, and CaddyWiper were used. CaddyWiper's task was to delete data on the attacked systems and thus make recovery more difficult. As in the 2016 attack, the attackers gained access to the energy system of Ukrainian providers through vulnerabilities in the ICS system. The attack was detected and stopped at an early stage by the cybersecurity authority CERT-UA in collaboration with ESET and Microsoft. There was no power outage.
NotPetya
NotPetya, believed to be another attack from the Sandworm side, is a cyberattack that began on June 27, 2017 and has had significant impact, primarily in Ukraine and Russia. Other countries from which there are records of an attack are the USA, Spain, France, UK, Germany, Netherlands, Poland, Norway, Italy, India and Australia. It is assumed that most of the other countries are also affected, but there are no records that can be found of them
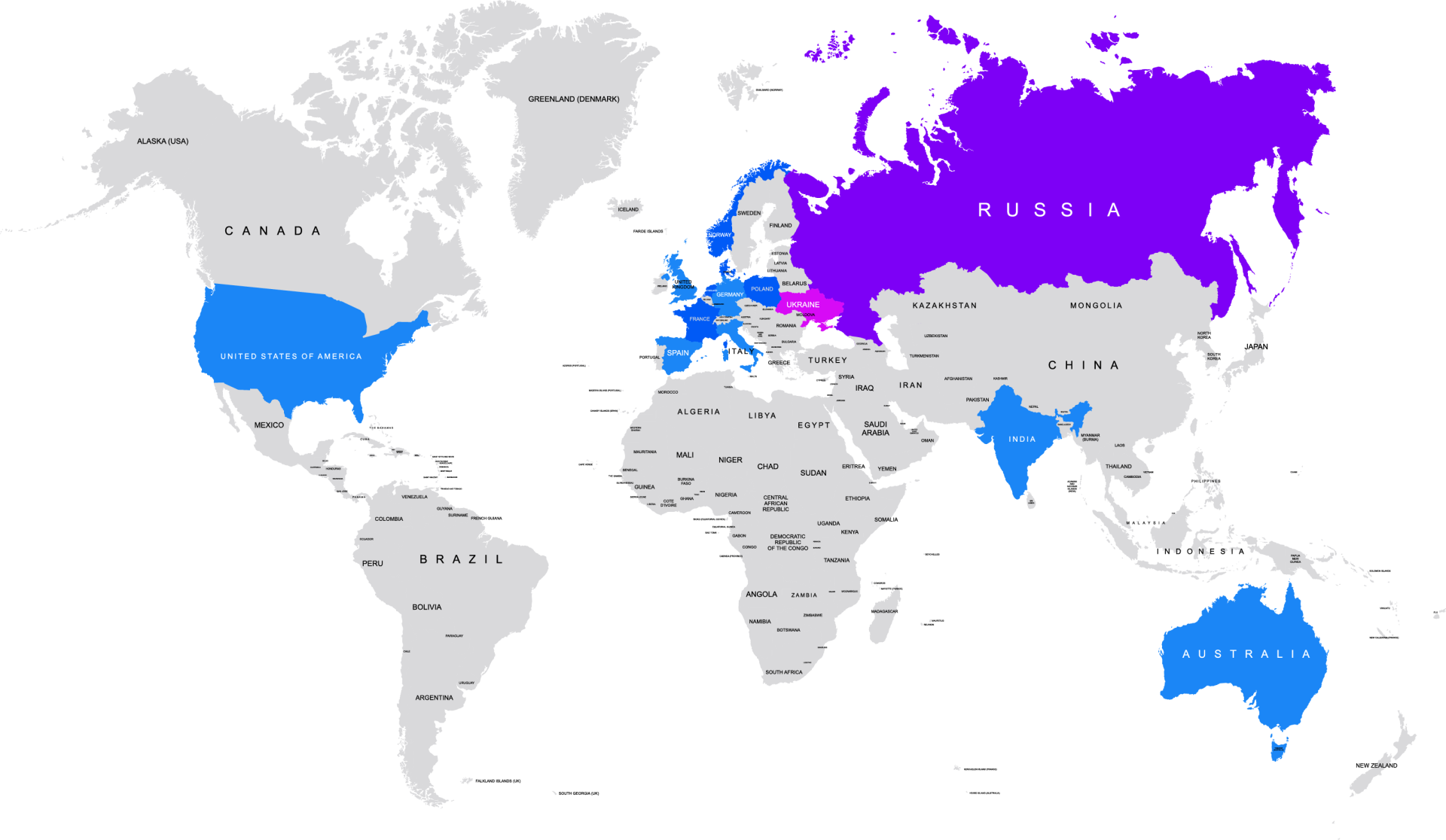
Due to the non-disclosure of the attack by some companies, it is difficult to give exact figures regarding the companies affected and the damage caused. However, if the approximately 2,000 companies affected are taken together and the long-term losses are included, the estimated damage is in the billions.
This ransomware is a wiper, i.e. a ransomware that only had destruction as its goal and therefore did not have money as its goal, as in most cases of hacker attacks.
The systems were initially infiltrated by the MeDoc software, a widely used Ukrainian accounting software, and thus had the first infiltrated systems in Ukraine, but this changed very quickly and affected several countries. As the origin is in Ukraine, this is considered cyber warfare by various sources.
Examples of affected companies are:
Maersk
• Danish logistics company
• Losses of around 300 million dollars
• Paralysis of global IT systems
• Shutdown of operations at many ports and terminals
Merck
• US pharmaceutical company
• Losses of around 870 million dollars
• Interruption of production and distribution
Mondelez International
• Food manufacturers (including Oreo and Cadbury)
• Losses of over 100 million dollars
• Interruption of production at various locations
FedEx (TNT Express)
• US logistics company
• Losses of approximately 400 million dollars
• Damage and recovery costs
Saint-Gobain
• French building materials group
• Losses of around 384 million dollars
• business interruptions and IT recovery costs.
Common Vulnerabilities and Exposures
Due to various security vulnerabilities, attackers such as Voodoo Bear are able to gain access to the systems of various companies and organisations. It is therefore important to always keep an eye on these and close them as quickly as possible to minimise the risk of an attack. To protect yourself specifically against Voodoo Bear, it is therefore also essential to look at the vulnerabilities that are known to be exploited by the aforementioned hacker groups.
CVE-2013-3906 - Microsoft Word
CVE-2013-3906 affects Microsoft Word and is caused by the incorrect processing of TIFF files. The vulnerability allows attackers to execute Remote Code Execution (RCE) through crafted TIFF images within a Word document. If the document is opened, malicious code can be executed on the target system without the user noticing.
This vulnerability was actively exploited by the hacker group Sandworm to carry out targeted attacks on government and corporate networks. The aim was to carry out espionage operations and steal sensitive information. Microsoft Word versions released before the security update of November 12, 2013 are affected.
CVE-2014-4114 - Microsoft PowerPoint
CVE-2014-4114 affects Microsoft PowerPoint and is known as a vulnerability in the OLE (Object Linking and Embedding) package manager. The vulnerability allows attackers to use specially crafted PowerPoint files to execute malicious code on the target system by loading external executable files undetected.
The Sandworm group used this vulnerability to carry out attacks as part of campaigns such as BlackEnergy, which compromised critical infrastructure, particularly in Ukraine. The aim was to gain operational control over networks and carry out targeted sabotage. This vulnerability affects Microsoft PowerPoint versions released before October 14, 2014, when Microsoft released the patch.
CVE-2021-44228 - Log4j
CVE-2021-44228, known as Log4Shell, affects the Java-based logging library Apache Log4j. The vulnerability allows attackers to execute remote code execution (RCE) on vulnerable servers by manipulating log inputs. By incorrectly processing JNDI lookups, attackers can load and execute malicious code, allowing them to gain full control of the target system.
The hacker group Sandworm specifically exploited this vulnerability to carry out attacks on critical infrastructure, including energy suppliers and government networks. Log4Shell was used to install backdoors and gain long-term access to systems. Log4j versions 2.0 to 2.14.1 are affected before a patch was released on December 6, 2021.
CVE-2021-26855 - Microsoft Exchange Server
CVE-2021-26855 affects Microsoft Exchange Server and is part of the attack series known as ProxyLogon. The vulnerability allows attackers to perform server-side request forgery (SSRF) and thus gain access to Exchange mailboxes or execute malicious code directly on the server.
The Sandworm group used this vulnerability to move laterally in corporate and government networks. Their aim was to read sensitive emails and carry out further attacks via compromised servers. Microsoft Exchange Server versions prior to the March 2, 2021 patches are affected.
Voodoo Bear Part 2 and Part 3
In Part 2 I will go into more detail about the software used, such as AcidRain, and in Part 2 about Hunting and Querries.
Similar hacker groups
In addition to Voodoo Bear, there are seven other Russian state-sponsored hacker groups.
Fancy Bear (APT28)
Alias: Fancy Bear, APT28, IRON TWILIGHT, SNAKEMACKEREL, Swallowtail, Group 74, Sednit, Sofacy, Pawn Storm, STRONTIUM, Tsar Team, Threat Group-4127, TG-4127, Forest Blizzard, FROZENLAKE
APT28 is also a constant threat alongside APT29, but unlike APT29 it is not subordinate to the Russian Foreign Intelligence Service (SVR), but to Russian military intelligence (GRU) or the Ministry of Defense. In addition to Ukraine and NATO, the group is also interested in Europe, South America, the Middle East and Central Asia.
There is also interest in various sectors such as government, military and defense, energy, finance, heavy industry, high-tech and telecommunications, higher education, news media, NGOs, and shipping and rail transport
Fancy Bear uses TTPs such as xTunnel, Mimikatz or Evil-Twin.
Cozy Bear (APT29)
Cozy Bear, primarily known as APT29, is believed to be under the control of the SVR.
There is also interest in various sectors such as biotechnology, consulting, education, financial services, government, healthcare, legal services, nonprofits, pharmaceuticals, technology, telecommunication, think tanks, travel, science/R&D
Voodoo Bear uses TTPs such as spearphishing attachments, Azure and M365 environment via Microsoft Graph API, password guessing and password spraying, exploit public-facing applications, FoggyWeb, GoldFinder, NativeZone and WellMess, RegDuke, PolyglotDuke, MiniDuke and FatDuke, SUNBURST, SUNSPOT and TEARDROP
Primitive Bear
Primitive Bear (aka Aqua Blizzard or Gamaredon) is also a Russian state-sponsored hacking group that has been linked to the Russian Federal Security Service (FSB). Just like Voodoo Bear, the main target is Ukraine, including government agencies, the military, non-governmental organizations, the judiciary, law enforcement agencies and non-profit organizations, as well as institutions related to Ukrainian affairs. This group also relied on espionage and exfiltration of sensitive data
Primitive Bear uses TTPs such as spear phishing emails, VBScripts, Ping, PowerPunch, Pterodo, QuietSieve, DinoTrain, DesertDown, DilongTrash, ObfuBerry and ObfuMerry
Venomous Bear
Venomous Bear is primarily known as Turla and, like Primitive Bear, is subordinate to the Russian Federal Security Service (FSB). According to Google, the group is primarily interested in Ukraine, NATO, Australia, South America, the Middle East and South-East Asia.
There is also interest in various sectors such as government, military and defense, higher education, news media and NGOs
Venomous Bear uses TTPs such as KOPILUWAK, QUIETCANARY, ANDROMEDA, Brute Force, Lateral Tool Transfer, Command and Scripting Interpreter: Python or Password Policy Discovery
Energetic Bear
Alias: TEMP.Isotope, DYMALLOY, Berserk Bear, TG-4192, Crouching Yeti, IRON LIBERTY, Energetic Bear, Ghost Blizzard, BROMINE, Dragonfly
Energetic is another Russian state-sponsored hacker group which, like Venomous and Primitive Bear, also belongs to the Federal Security Service of the Russian Federation (FSB). This group is active worldwide.
As the name suggests, the sector most likely to be affected is the energy sector. However, the sectors Chemicals, Communications Infrastructure, Consumer Retail: Hardline (Consumer Durables), Defense Industrial Base, Digital, Print and Broadcast Media, Education: Higher Education, Financial, Services, Healthcare & Public Health, Transportation Systems: Aviation are also affected
Energetic Bear uses tools such as Trojan.Karagany, Backdoor.Oldrea and CrackMapExec, and the techniques used include account manipulation, password cracking and supply chain compromise.
Ember Bear
Alias: Saint Bear, Lorec Bear, Bleeding Bear, DEV-0586, UNC2589, UAC-0056, Lorec53, Ember Bear
Just like Fancy Bear and Voodoo Bear, Ember Bear is probably part of the General Staff of the Armed Forces of the Russian Federation (GRU). In addition to Ukraine and Georgia, Western Europe and North America are also targets of the attacks.
The three sectors are mainly target ministries, pharmaceutical companies, and financial sector
According to MITRE, the tools that could be tracked are ATT&CK WhisperGate, Saint Bot, OutSteel, as well as techniques such as Software Packing, User Execution: Malicious File, Exploitation for Client Execution
Boulder Bear
Alias: -
Another hacker group that can be linked to the Russian state is Boulder Bear. There is virtually no information on this, except that it is possibly subordinate to the Federal Security Service of the Russian Federation (FSB).
Countries or sectors at risk, as well as TTPs, are unfortunately not known.
For further research
https://www.youtube.com/watch?v=QSVQR_7fAFQ
https://cloud.google.com/blog/topics/threat-intelligence/sandworm-disrupts-power-ukraine-operational-technology/?hl=en
https://services.google.com/fh/files/misc/apt44-unearthing-sandworm.pdf
https://cloud.google.com/blog/topics/threat-intelligence/apt44-unearthing-sandworm?hl=en
https://attack.mitre.org/groups/G0034/
https://security.microsoft.com/intel-profiles/cf1e406a16835d56cf614430aea3962d7ed99f01ee3d9ee3048078288e5201bb?tab=description&tid=50271394-6aac-43fb-bd75-a0b7f111fbea
https://safereach.com/en/blog/apt44-sandworm-threat-companies/
Attacks
https://www.wired.com/story/cyber-army-of-russia-reborn-sandworm-us-cyberattacks/
https://media.defense.gov/2020/May/28/2002306626/-1/-1/0/CSA Sandworm Actors Exploiting Vulnerability in Exim Transfer Agent 20200528.pdf
https://www.justice.gov/opa/press-release/file/1328521/download
https://www.justice.gov/opa/pr/six-russian-gru-officers-charged-connection-worldwide-deployment-destructive-malware-and
Viasat
https://open.spotify.com/episode/3ad56QrgnXLuyeHfwphzC3?si=UYK32FJHSEaVvvU8n4VMPw
https://news.viasat.com/blog/corporate/ka-sat-network-cyber-attack-overview
https://www.linkedin.com/in/zhora/?originalSubdomain=ua
https://therecord.media/second-cyber-official-detained-zhora
https://www.bbc.com/pidgin/world-60598588
https://www.groundcontrol.com/blog/how-satellite-iot-closes-the-gap-in-remote-wind-turbine-data-monitoring-challenges/
NotPetya
https://blog.talosintelligence.com/worldwide-ransomware-variant/
Ukraine Electric 2016
www.dragos.com/wp-content/uploads/CrashOverride-01.pdf
https://web-assets.esetstatic.com/wls/2017/06/Win32_Industroyer.pdf
https://www.cisa.gov/news-events/ics-alerts/ir-alert-h-16-056-01
CaddyWiper (2022)
https://www.cisa.gov/news-events/analysis-reports/ar22-115c
https://www.dragos.com/blog/new-details-electrum-ukraine-electric-sector-compromise-2022/


